Known Bluetooth standard version vulnerabilities
BR/EDR
BLE
Throughout the history of the Bluetooth standard, security issues have been identified and have led to vulnerabilities. Devices with Bluetooth capabilities rarely implement only the latest version of the standard, instead, for compatibility reasons, support earlier versions that may have unresolved security issues.
As with vulnerabilities in the driver and stack, it’s necessary to verify which vulnerabilities of the standard affect the analyzed device.
It should also be noted that the different Bluetooth specifications have a lifecycle announced by the Bluetooth SIG. It is important that the used Bluetooth specification version will be supported during the product lifecycle because if new vulnerabilities in the standard appear, they will not be fixed.
Description
First, the version of the Bluetooth standard supported by the device must be identified. The implemented version of the standard can be obtained from different sources:
- Inspection of the packets of a connection at the
Link Layeror link layer (LMPorLLL) forLMP_VERSION_REQ,LMP_VERSION_RESandLLL_VERSION_INDpackets. - Requesting version data from the device via the HCI
Read remote versioncommand. - Device information inspection: devices like smartphones usually specify the Bluetooth version among their features.
- Searching to obtain the public information of the device: device models sometimes indicate the Bluetooth version they implement.
- Requesting data from the manufacturer.
It should be borne in mind that information provided on the Internet may be outdated and it’s advisable to contrast it, whenever possible, with the information provided by the device.
Vulnerability enumeration can generally be done by searching in vulnerability databases or general-purpose search engines.
Checking the Status of the specification version can commonly be found in the list of Bluetooth SIG documents.
The most common specifications and their status as of May 2023 are listed below:
| Version | Status | Deprecation | Withdrawal |
|---|---|---|---|
| Core Specification 4.0 | Withdrawn | 28/01/2019 | 01/02/2022 |
| Core Specification 4.1 | Withdrawn | 28/01/2019 | 01/02/2023 |
| Core Specification 4.2 | Adopted | 01/02/2026 | 01/02/2031 |
| Core Specification 5.0 | Adopted | 01/02/2027 | 01/02/2032 |
| Core Specification 5.1 | Adopted | 01/02/2029 | 01/02/2034 |
| Core Specification 5.2 | Adopted | 01/02/2030 | 01/02/2035 |
| Core Specification 5.3 | Adopted | 01/02/2032 | 01/02/2037 |
| Core Specification 5.4 | Adopted | 01/02/2033 | 01/02/2038 |
Related resources
Listed below are some resources that may be useful for obtaining the Bluetooth version supported by a Bluetooth device:
| ID | Description |
|---|---|
| BSAM-RES-04 | Bluetooth connections sniffing |
| BSAM-RES-05 | Capture of a Bluetooth connection |
| BSAM-RES-06 | Enabling debug mode on a Bluetooth controller |
| BSAM-RES-07 | Sending and receiving HCI messages |
For vulnerability enumeration the following resources may be of interest:
| ID | Description |
|---|---|
| BSAM-RES-03 | Vulnerability database search |
Example case
A connection that established between our PC and a device is captured using the resource BSAM-RES-05 (Capture of a Bluetooth connection). This capture has been done with the debug modes of a Cypress card enabled following the BSAM-RES-06 (Enabling debug mode on a Bluetooth controller) technique. In this way, packets from the Link Layer are captured, in this case from BR/EDR.
Among the exchanged packets, an LMP_VERSION_RES packet is found.
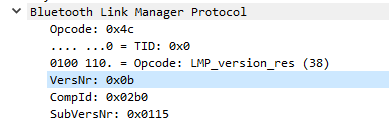
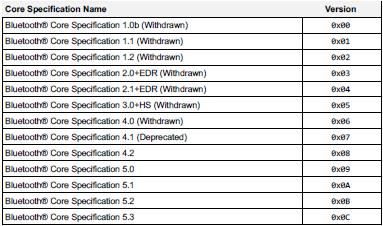
The dissected packet has a VersNr field with value 0x0b. By consulting the Bluetooth Assigned Numbers Rev. 2022-12-20 document in Section 2.1 (Core specification versions), it is concluded that the device under test supports Bluetooth v5.2.
A search following the resource BSAM-RES-03 (Vulnerability database search) finds three vulnerabilities against this version of the Bluetooth standard:
For each of the vulnerabilities found, a proof of concept is executed. It is found that the analyzed device does not accept low entropy keys and is therefore considered not vulnerable to KNOB. However, the device allows authentication of devices with cloned identities and is therefore considered vulnerable to BIAS and BlueTrust. The controller manufacturer is notified of this security issue to obtain a firmware update to address the vulnerabilities found.
External references
- Bluetooth Core V5.3, Vol. 6, Part B, Section 2.4.2.13 - LL_VERSION_IND
- Bluetooth Core V5.3, Vol. 2, Part C, Section 4.3.3 - LMP version
- Bluetooth Core V5.3, Vol. 4, Part E, Section 7.1.23 - Read Remote Version Information command
- Bluetooth Core V5.3, Vol. 4, Part E, Section 7.7.12 - Read Remote Version Information Complete event
- Bluetooth Assigned Numbers Rev. 2022-12-20, Section 2.1 - Core specification versions
