Pairable mode by default
BR/EDR
BLE
The first step when using a Bluetooth device is pairing, at which time trust is established between the two to allow future connections. This pairing for security reasons must require user validation and supervision so that a new pairing attempt can validate or cancel the process.
Devices configured to answer to pairing requests without user intervention allow the extraction of part of the information necessary to be impersonated (MAC, Name, Bluetooth Version supported…). It is recommended to prevent a device from being paired with other devices if it is not necessary. Preferably, the pairing mode should require physical user intervention such as pressing a button.
A paired device can make requests and interact with the audited device and may therefore pose a security risk if the device contains sensitive information.
Description
It must be proven that it is only possible to pair with the device by changing its status to pairable. The change of mode to pairable mode must require user intervention to be enabled. Pairable mode must be enabled for a limited time, until a pairing is performed, or the user manually deactivates the status.
Related resources
To check if the device is pairable, a pairing process can be initiated with user tools or by using libraries such as Scapy. From the resources section, the following may be useful:
| ID | Description |
|---|---|
| BSAM-RES-04 | Bluetooth connections sniffing |
| BSAM-RES-05 | Capture of a Bluetooth connection |
| BSAM-RES-06 | Enabling debug mode on a Bluetooth controller |
| BSAM-RES-07 | Sending and receiving HCI messages |
Example case
A Bluetooth headset is discoverable and pairable after it is turned on. During that time, another unpaired device can access information about these headsets through pairing requests without the user being notified.
We will use Wireshark with BTVS (btvs.exe -Mode wireshark) to capture packets for analysis.
We are pairing headphones with the laptop, which initiates a new connection by requesting the input/output capabilities, ‘IO Capability,’ with the IO Capability Request command:
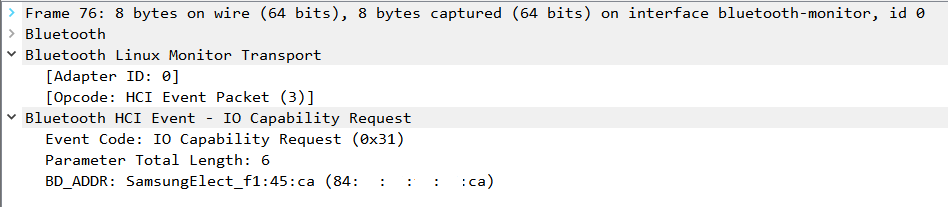
The headphones, at that moment, allow the connection as they respond with ‘IO Capability’ using the IO Capability Request Reply command:
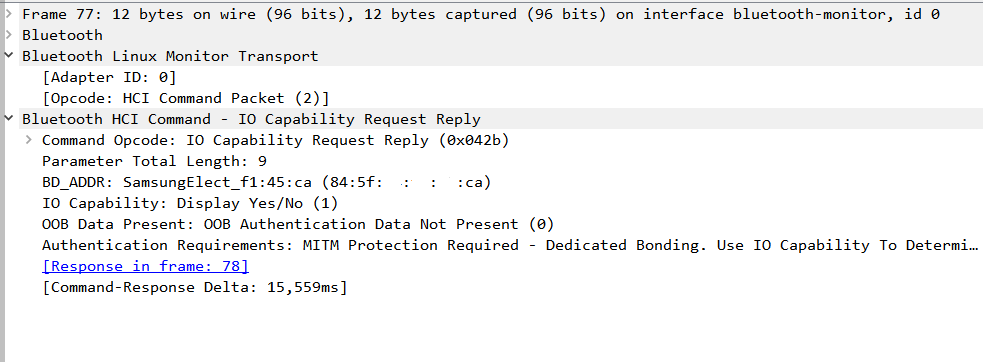
The procedure culminates with the establishment of the connection, notified by the Simple Pairing Complete command:
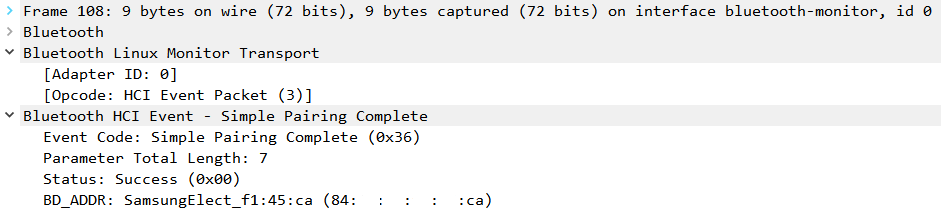
The check control FAIL because the device is pairable by default.
