Pairing without user interaction
BR/EDR
BLE
In Bluetooth, it is necessary to establish a shared link key between two devices to encrypt communications. The pairing procedure “introduces” both devices to each other and establishes the shared key. There are different methods to establish the shared key, and some of these do not implement security controls to verify the identity of the involved devices.
The just works method allows pairing using a numerical key, which is done without user interaction, and does not implement measures to ensure that the devices are known to the user. All the cryptographic material used for a just works connection during the pairing process is sent over the Bluetooth band without any encryption, making it possible to capture this information with a sniffer and impersonate the device.
Additionally, if the pairing mode is legacy, it is susceptible to man-in-the-middle (mitm) attacks.
Description
The following two elements must be checked to verify that the control is satisfied:
- The “Authentication requirements” field of the “IO Capability Response” message must show a value with MITM protection.
- The device shall reject any pairing attempt that requires the “just works” method.
The “IO Capability Response” message, which contains the “Authentication Requirements” field, can be captured during a pairing with a user tool or by using Scapy to simulate a partial pairing.
To verify that it is not possible to pair using the “just works” method, one can first check what capabilities the audited device has, and secondly, configure a local device with the necessary capabilities to downgrade the pairing method to “just works”.
The control is only fulfilled when using a value for “Authentication Requirements” that includes MITM protection and it is not possible to pair with “just works”.
Related resources
To check this control, the following resources may be useful:
| ID | Description |
|---|---|
| BSAM-RES-04 | Bluetooth connections sniffing |
| BSAM-RES-05 | Capture of a Bluetooth connection |
| BSAM-RES-07 | Sending and receiving HCI messages |
| BSAM-RES-09 | Changing the attributes of a controller |
Example case
In this example, a pairing test with wireless headphones is demonstrated.
For the test, Wireshark has been used with BTVS (check out the resources section) to capture and analyze packets. To perform the connection and pairing, the Bluetooth device configuration tool of the laptop’s operating system is used.
The headphones use Bluetooth Classic, where most of the pairing process occurs in the controller and is not visible from the host. However, in this case, it is sufficient to observe the exchange of HCI messages, where the IO Capability values appear.
The first HCI messages of the pairing process between the two devices are the IO Capability Request event, where the controller requests the local host’s IO Capabilities, and the IO Capability Request Reply command, where the host responds. These messages are not relevant for the current example.
Later, the IO Capability Response message is observed, where the headphones’ IO Capabilities appear. In this case, it is observed that the value is 0x03 (NoInputNoOutput).
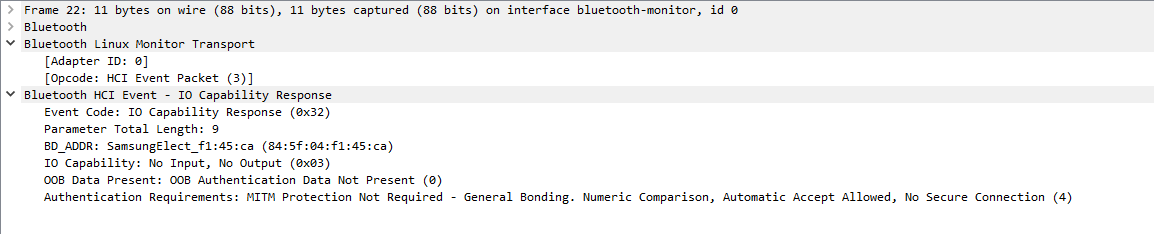
This value does not allow pairing to be done with user interaction. In the capture, it is observed that the pairing is indeed completed successfully. Pairing is confirmed through the Simple Pairing Complete command.
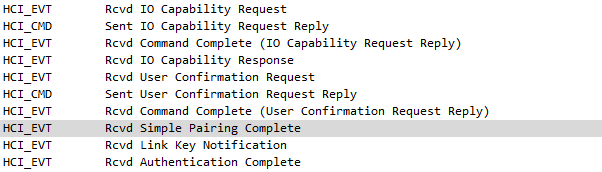
The input/output capabilities of the headphones have allowed pairing without user confirmation or notification.
The control result will be FAIL when a device is pairable without user intervention.
The Just Works pairing mechanism should be avoided. In this case, the device had buttons on both headphones and can be used as Yes/No buttons, thus confirming the pairing.
Full capture: Galaxy Buds Pairing
External references
- Bluetooth Core V5.3, Vol. 3, Part C, Section 5.2.2.4 - IO capabilities
- Bluetooth Core V5.3, Vol. 3, Part C, Section 5.2.2.5 - Mapping of input / output capabilities to IO capability
- Bluetooth Core V5.3, Vol. 3, Part C, Section 5.2.2.6 - IO and OOB capability mapping to authentication stage 1 method
- Bluetooth Core V5.3, Vol. 3, Part H, Section 2.3.2 - IO capabilities
- Bluetooth Core V5.3, Vol. 3, Part H, Section 2.3.5.1 - Selecting key generation method
- Bluetooth Core V5.3, Vol. 3, Part H, Section 2.3.1 Pairing Methods
- Bluetooth Core V5.3, Vol. 3, Part H, Section 2.3.5.2 LE Legacy pairing - Just Works
- Bluetooth Core V5.3, Vol. 3, Part H, Section 2.3.5.4 Out Of Band
- Bluetooth Core V5.3, Vol. 3, Part H, Section 2.3.5.6.2 Authentication Stage 1 - Just Works or Numeric Comparison
