Smart Meters – The Spanish Scenario and the Telemanagement System
Table of Contents
Smart meters have become a reality in recent years not only in new housing, but also in older buildings where—by legal requirement—they have had to renew their measuring devices. In particular, and in accordance with Order IRC /3860/2007 of the 28th of December, all electricity meters supplied with a contracted power of up to 15 kW should have been replaced by equipment which allows time-based pricing and remote management by the 31st of December 2018.
Integrated into the concept of smart grids, the computerization of the electricity distribution infrastructure is not only an opportunity to improve the efficiency of the management and use of it, but also an implementation challenge from the point of view of cybersecurity, with new networks, protocols and attacks. In this regard, the EU has anticipated the problem and the Smart Grid Task Force’s expert group 2 has begun to work on a series of regulatory recommendations, which can be found in the following link.
In order to understand the type of threats that these meters may face and the infrastructures in which they are integrated, we must first understand the different agents that make up the Spanish electricity system. Some of the systems and technologies mentioned below are common in other countries. Let’s get to it.
The electricity system in Spain
Since the liberalisation of the Spanish electricity sector in 1997 by transposition of the European directive, the entire process of electricity supply has been divided into four phases, namely:
- Generation: is responsible for producing electricity through the exploitation of a natural resource.
- Transport: is in charge of transmitting this energy from the generation plants to different areas using the transport network (consisting of high voltage lines). The forwarding agent is also known as the Network Operator, which today is Red Eléctrica de España .
- Distribution: is responsible for transmitting energy from the transmission grid to the supply points (i.e. companies or individuals’ meters). The agents in charge of distribution are the distribution companies, and each of them is in charge of distribution in a particular geographical area, which is why they are considered “natural monopolies”.
- Commercialization: is responsible for selling electricity to consumers.
The electricity meters are managed by the distributor, which measures consumption levels and gives them to the marketer, who in turn is responsible for collecting the electricity bill from the consumer. At the same time, the distributor is in charge of ensuring contracted power limits are effective. They take measurements, cut or reconnect supply points, amongst other things, as appropriate.
The introduction of smart meters greatly simplifies the above tasks through the remote management functionality, which allows the distributor to remotely control various aspects of the supply point without on-site intervention. This automation is possible through the infrastructure described below.
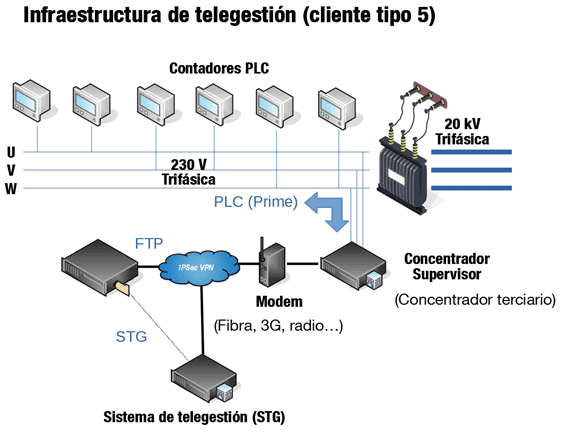
The Telemanagement infrastructure
In order to understand the type of threats to which smart meters are subjected, we must begin by understanding the structure of the system to which they belong. In the case of home smart meters, they communicate via PLC to a device owned by the distributor known as Tertiary Concentrator. This device is usually found in prefabricated buildings called Transformer Substations, whose main objective is to protect the transformer from voltage changes.
Tertiary Concentrators, in addition to serving as intermediaries between the meters and the distributor, can also perform monitoring functions. For example, they measure the energy circulating through the transformer in order to detect fraudulent use of the electrical flow by remaining vigilant at all times to ensure that there are no deviations between the sum of power of all the meters and that measured at the output of the transformer.
The concentrators communicate with the distributor via several IP channels (radio, fiber, 3G…), often with a second level of protection based on VPN networks. The distributor, in addition to storing the measurements through FTP, can communicate back to the concentrators, requesting a change of the contracted power of a particular meter, billing periods, connection and disconnection of the electrical network, or even a firmware update. Therefore, the infrastructure is as follows:
The Start of the Supply Chain: The Extreme PLC
In Spain, most PLC communications between meters and concentrators are realised through two protocols called DLMS/COSEM (in the application and network layer) and PRIME (in the physical and link layer). DLMS/COSEM is actually the combination of two different protocols: on the one hand, DLMS offers message exchange functions between devices and, on the other, COSEM facilitates the use of meters as servers to which some customers can make certain requests, following an object-oriented model.
With regard to cybersecurity, both protocols have communication security features such as encryption, authentication and authorization. DLMS/COSEM offers three levels of authentication security (unauthenticated, password authenticated, and authenticated in four steps with shared secrecy) and different levels of transport security related to message encryption and authentication. The security policy is determined on the basis of the type of access that the client requests to the COSEM server, i.e. the more privileged operations may require more restrictive security policies.
On the other hand, PRIMEas a physical and link layer, limits security to message encryption and authentication. The security of this protocol is based on three security profiles numbered 0 to 2, where 0 would represent the total absence of security and levels 1 and 2 different levels of protection.
Considering that both protocols provide adequate measures to ensure information security, these protocols’ greatest weaknesses can be reduced to implementation errors and an excessively lax security configuration.
A photograph of the system from the supply point
The presence of these security profiles suggests a starting point for cybersecurity audits on these types of OT networks. So what is the default security setting (both in PRIME and DLMS/COSEM) on a smart meter network?
In order to be able to answer this question we first need access to a network of smart meters. Nowadays this is not a problem since practically any plug gives visibility to the PLC network of the meters connected to the local concentrator and, in some cases, meters connected to other concentrators.
Secondly, we need a PLC modem compatible with PRIME. This is not so easy: although there are indeed devices aimed at debugging and analysing PRIME, they are so expensive and have such limited functionality that their ability to be used for an in-depth audit is reduced. Instead, the best value for money option is a PLC evaluation board. These evaluation boards are offered by hardware manufacturers at moderate prices (less than €500) so that potential customers can study the feasibility of this technology for a future wholesale purchase. In addition, they often include code examples and case studies for the development of firmware, which can be very useful in writing specialized auditing tools.
For this test, an ATPL360-EK evaluation board which includes PRIME and G3 libraries, offered by Microchip, is needed. In addition to a series of test applications, including a PRIME-compatible PLC sniffer.
This PLC development board includes a suite of test tools (https://www.microchip.com/DevelopmentTools/ProductDetails/PartNo/ATPL360-EK?utm_source=MicroSolutionstm_medium=Articletm_content=DevToolstm_campaign=StandAlone) including a Sniffer PLC for Windows systems. After acquiring the corresponding firmware (also distributed by Microchip) and integrating it into the development boards, all you have to do is connect the board to the electrical network and with USB to PC connection, use this software to start examining the frames.
First results of PLC network security analysis
Two tests were carried out to measure PLC traffic over the course of a day in two districts of Madrid, with very similar results. It should be noted that the tools mentioned above only scan up to the link layer (PRIME). The DLMS/COSEM top layers should be analysed by extracting the contents of the PRIME frames.
The tests, carried out in a residential neighbourhood home and an office building, measured up to a hundred meters. Because the MAC address (also called EUI-48) of the meters is only exchanged during the registration process on a given subnet, only a fraction of all visible nodes is known. However, the different meters can still be operated through an identifier assigned during the registration process called LNID (Local Node Identifier).
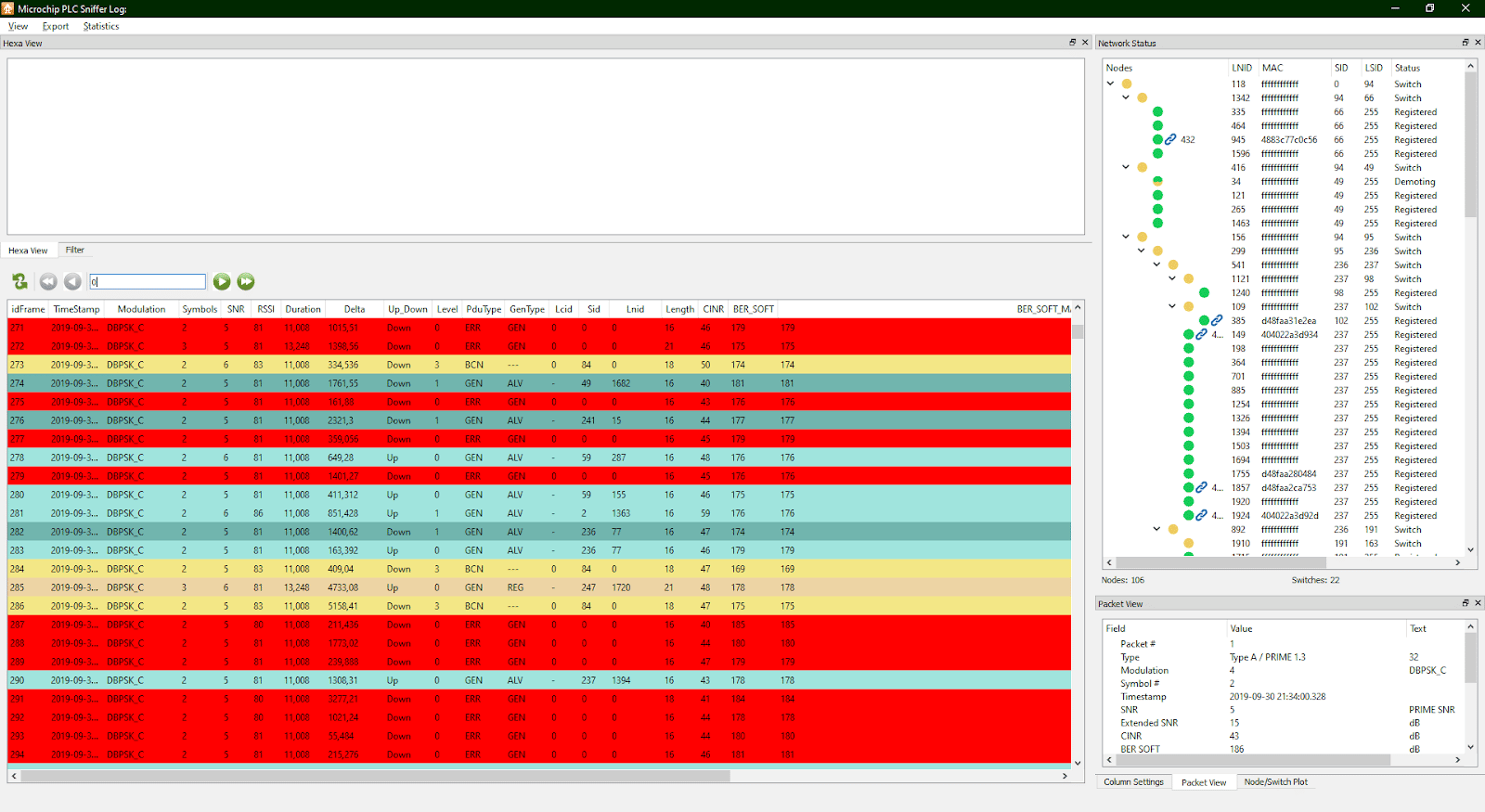
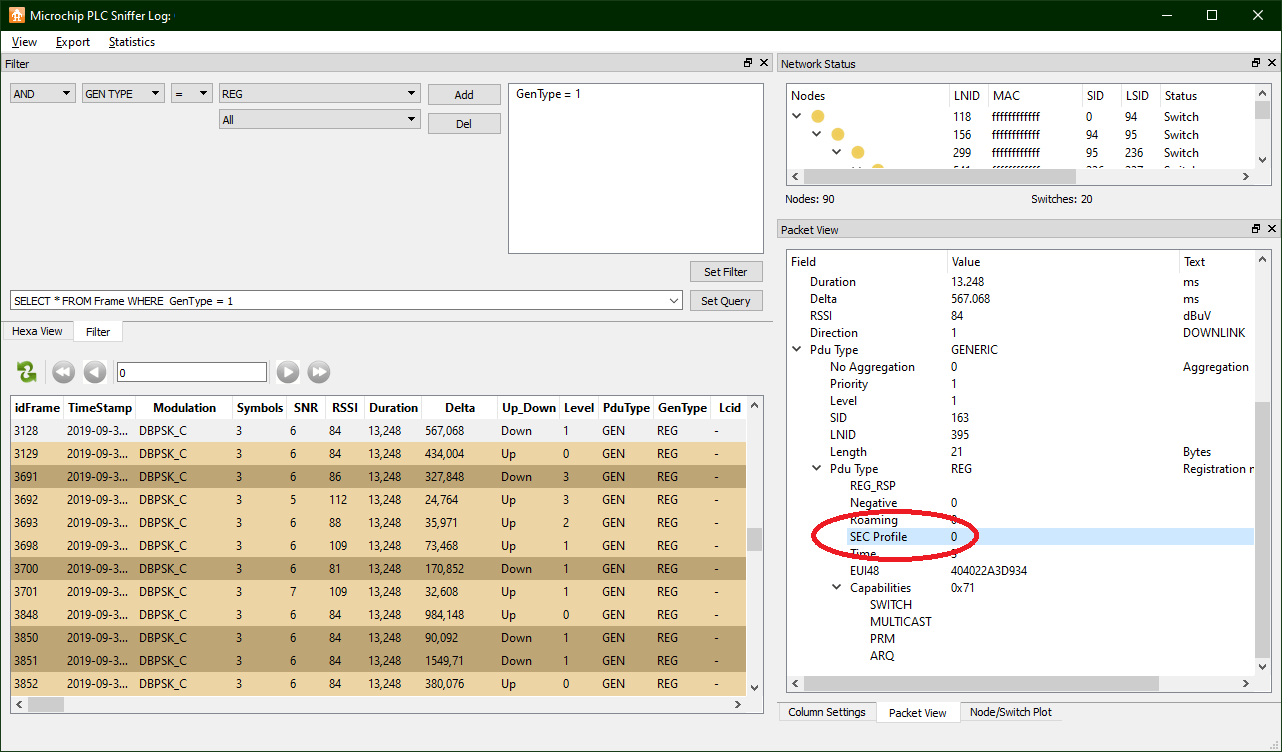
PRIME traffic frames are grouped into two main categories: control and data, the former being present most of the time. One of the most interesting control frames is the registration frame, in which the security profile used in the communications between the meter and the concentrator is worked out. Fortunately, Microchip’s Sniffer PLC allows you to filter packets in multiple ways through intuitive SQL queries:
This is evident as the registration frames are requesting a security profile 0 at link level: i.e. clear messages without any security measures.
The security measures, if any, are then left for the higher layers, corresponding with the DLMS/COSEM traffic between meters and concentrators.
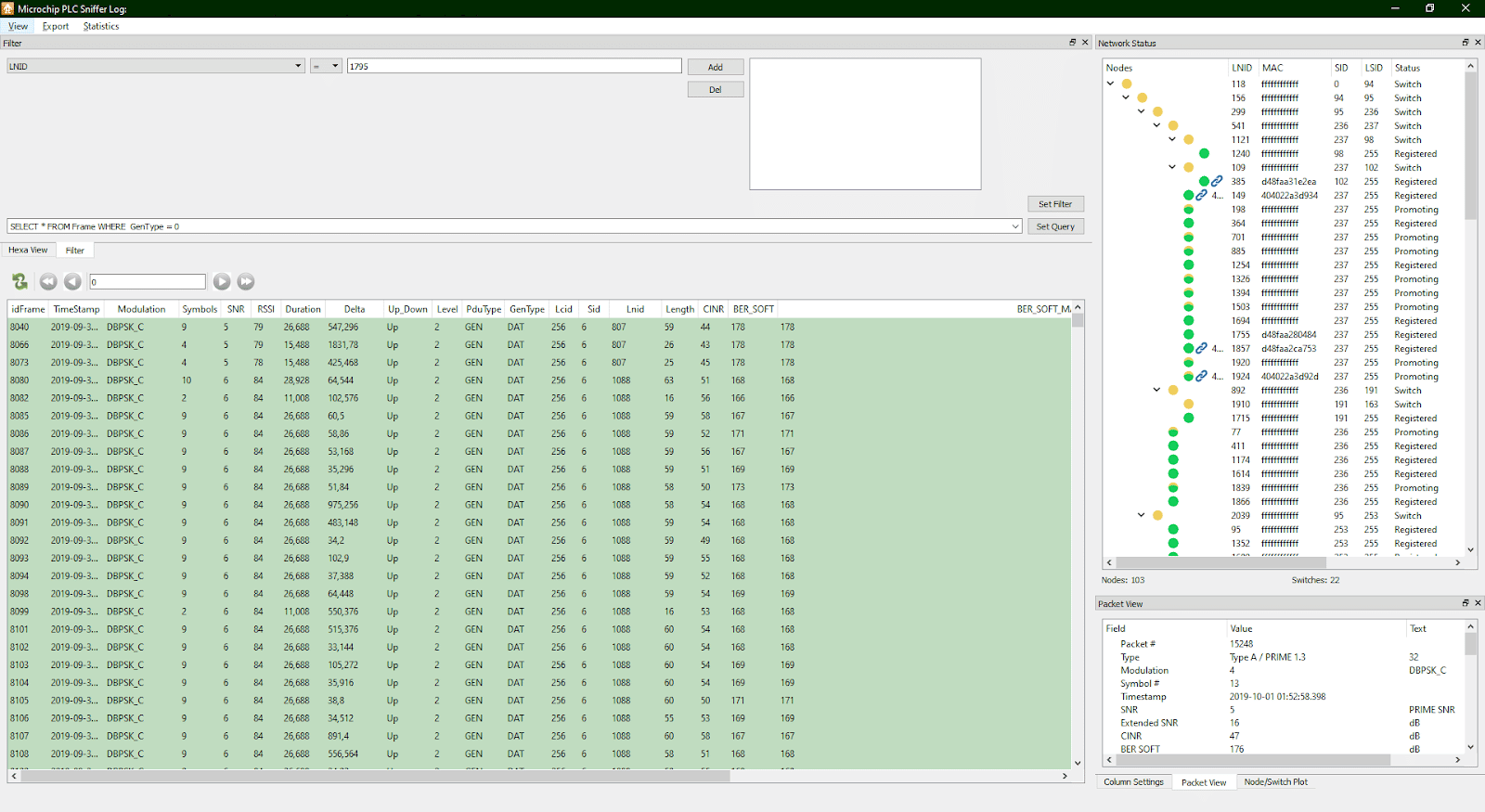
Determining whether encrypted DLMS traffic is as simple as analysing DATA-type PRIME frames and examining their contents. So it’s necessary to:
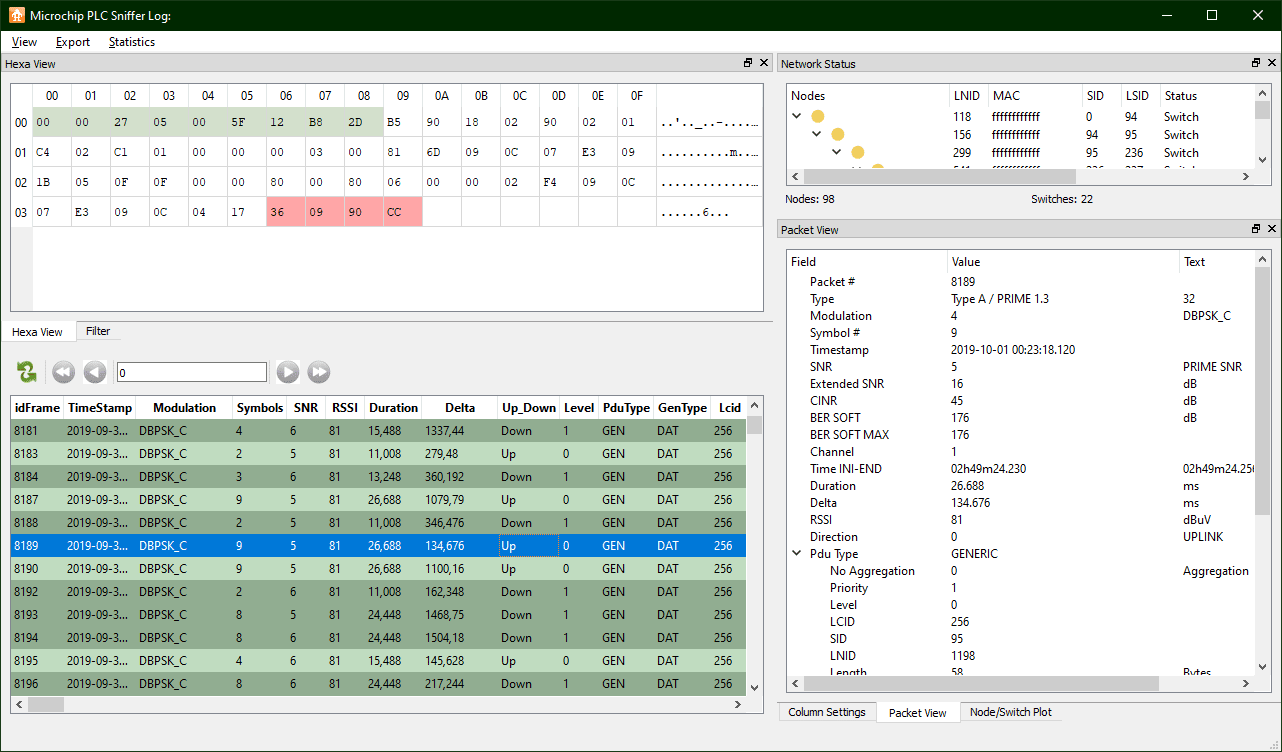
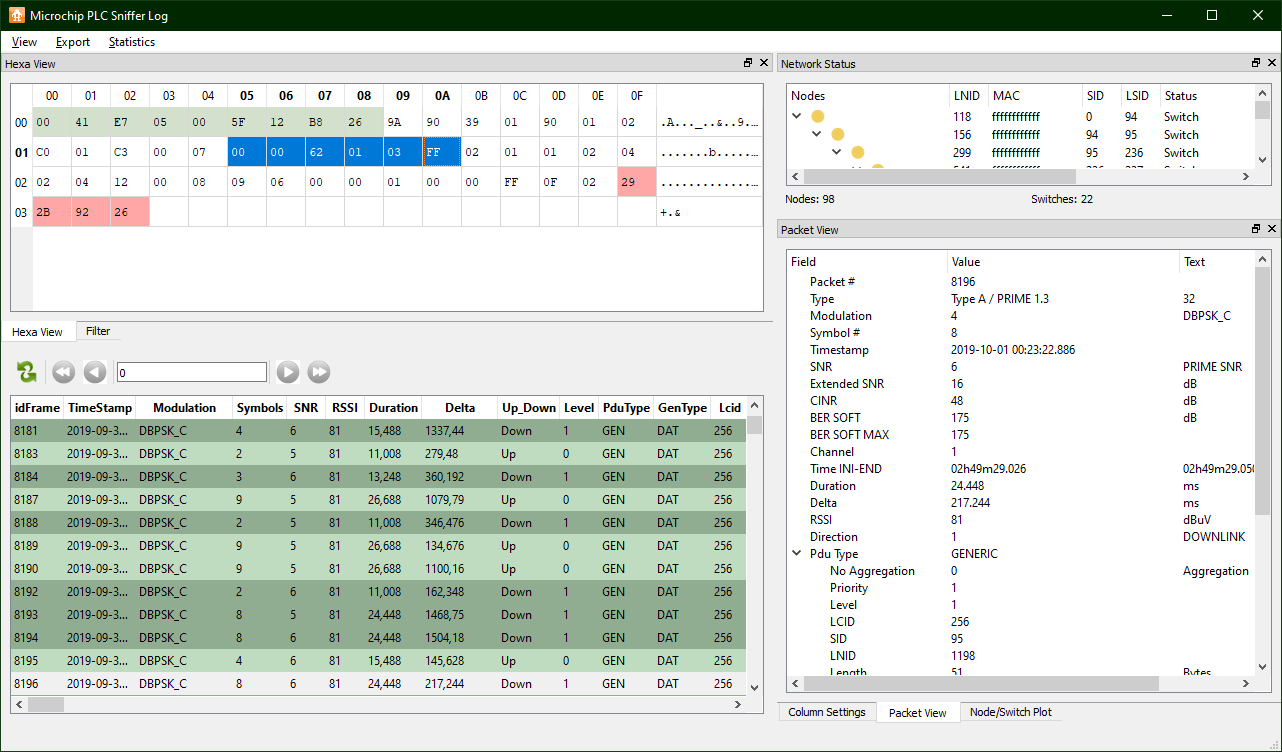
Obtain a PLC Sniffer that also includes a hexadecimal view that allows you to examine the contents of the frames. Because one of the consequences of using an encryption system is almost always an increase in the entropy of message information, an imbalance between the number of ones and zeros in a message suggests that no coding encryption mechanism is being used. This is exactly what is observed in all the frames:
You can go further and try to determine if PRIME is including DLMS traffic. This can be achieved by knowing that DLMS messages refer to COSEM objects, which are routed through an object code (called OBIS code) consisting of 6 consecutive bytes. These 6 bytes are usually represented both in hexadecimal notation without separators and in decimals without being separated by dots. In addition, COSEM objects refer to different measurements and parameters that a meter can report, and their OBIS codes are tabulated. A distinctive feature of OBIS codes is that at many times they contain one or more zeros and usually end in 255, so identifying them in a frame, even if you don’t know its structure, is quite easy. It has been observed that the presence of byte 0xff (corresponding to decimal number 255) is generally infrequent, and is usually found almost always in the first frame of a fragmented packet. Effectively:
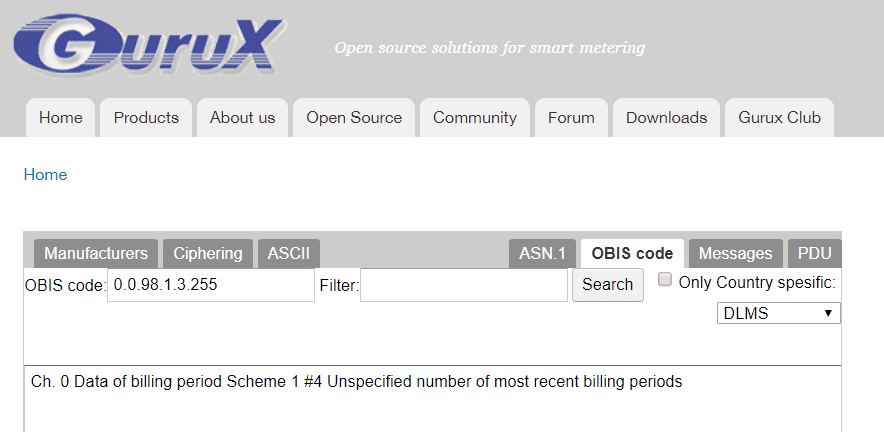
The bytes highlighted in the selected PRIME data frame appear to correspond to an OBIS code 0.0.98.1.3.255. By entering this identifier in Gurux’s online tool (https://www.gurux.fi/GuruxDLMSTranslator) you get the following description:
That is, the message appears to contain consumption data on the latest billing periods, without specifying the limit. This is consistent with what is expected from an electricity meter. Further analysis of the fragmented packets reveals rather low entropy content, so the presence of HMAC codes seems equally unlikely. So the above results suggest that no security measures are being implemented (both from the point of view of confidentiality and authenticity) in PLC traffic exchanged between meters and concentrators.
In the next article in this series we will continue to discuss how to assess meter security risks. Bearing in mind that the lowest security profiles appear to be the norm in the observed outlets, the following tests will be aimed at sending privileged orders to meters and in order to understand what kind of mitigation measures exist to prevent their exploitation.
Discover our work and cybersecurity services at www.tarlogic.com
This article is part of a series of articles about Smart Meters
- Smart Meters – The Spanish Scenario and the Telemanagement System
- Smart Meters – Threats and Attacks to PRIME Meters
- Smart Meters – A proof of concept: hacking a smart meter
- Smart Meters – Assessing Concentrator Risk
- Security in PRIME networks – Current status
- PLCTool, the Swiss army knife of smart meters
- PLCTool plugin support