Dynamic Cybersecurity Risk Assessment

Chapter II. Constant changes in information systems and the evolution of threats make it necessary to continuously update the cybersecurity risk status.
If we think about temporary point of view of cybersecurity risks, when assessing the risk of an asset, we probably could differentiate between two types:
There would be firstly the dynamic cybersecurity risk that contrary to static one, complies with temporal parameters necessary to arrive at its calculation in an updated, or dynamic way. Secondly, there is the static risk, whichis the risk that is evaluated at a given time, but is not updated frequently.
Faced with a situation of changes produced by for example, software updates, static risks my not provide sufficiently up-to-date state of security metrics, which is certainly a risk itself.
Dynamic Cybersecurity Risk could then be more effective if we want to obtain the risk state of an asset or group of assets and generally of our company at a given point in time, if it is continuously updated.
In order to maintain cyberrisk state, threats and vulnerabilities need monitoring processes in a regular basis, since it is necessary to know changes that can occur, to update the security metrics that give rise to the risk calculation (probability and impact).
Carrying out vulnerabilites priorization process is essential to arrive at the metrics needed. It is an effective practice to start this process by assessing the security health state of assets and thus determine which vulnerabilities need to be addressed with greater urgency, and which assets are at greater or lesser risk at the beginning of the process.
This is a snapshot using security health parameters such as: technological design, safeguards and/or security controls, and vulnerabilities identified. This is all part of an overall cybersecurity risk analysis and threat priorization.
Constant changes in information systems modify the initial risk state, which means that in many cases the first entries in a risk analysis are different from those used to subsequently assess the exposure of an asset, and, the company in general, having to repeat the process in last case, prior to a final security assessment.
Due to this fact, the accuracy of risk assessment may decrease, causing uncertainty to increase over time if variables involved in risk assessment are not updated when due.
ISO 27001 normative, for example, talks about the Deming Cycle or PDCA cycle (Plan, Do, Check, Act). The Deming Cycle establishes a process where risk analysis is repeated over defined periods of time, and planning is adapted to the new risk scenario. NIST (National Institute of Standards and Technology) also defines a six-step methodology for managing risks, which is iterated throughout the life cycle of IT systems. While of course these methodologies are correct, they can produce a false sense of dynamism if they are not used frequently and iterations take place over discrete (and usually long) periods of time.

There are several factors that must be taken into account in risk management, and which are subject to certain randomness, which can be grouped into 4 sets:
- Changes in information systems: Mainly addition, modification or deletion of assets, as well as alterations in maintenance services, resources, and suppliers supporting the information systems.
- Zero-day vulnerabilities and/or new threats detected: But also unknown threats and vulnerabilities, which affect the organization’s assets.
- Evolution of threats: already known, and finally, monitored threats that cause an incident (intentional or unintentional).
- Security measures: Modify the expected impact, and the probability of a threat damaging an asset.
When any of the above components in the information systems or their environment undergoes a change, the risk analysis entries should be updated to reflect that state, yielding new results that help assess the overall security risks in the organization.
Although “dynamic risk analysis” is not a new term, it is the most repeated term, and is based primarily on a periodic update of the risk analysis variables that define the information system. The terminology can be seen in some authors with terms such as “on-line risk assessment” or “real-time risk assessment” as a synonym for “dynamic risk assessment”.
The dynamic cybersecurity risk assessment process as such does not differ from that defined in a traditional risk analysis in terms of the methodology used at the outset.
However, it introduces an additional parameter that is dynamic in nature and helps to determine more accurately the state of the risk at a given point in time.
For this purpose, we take into account the state of the vulnerability within its life cycle, as the parameter with propensity to change.
- Exploitable
- Identified
- Mitigated
- Remediated
Depending on vulnerability state within its life cycle, different levels of criticality are assigned. We can interpret the state within the lifecycle as a parameter that helps us to determine the greater or lesser probability that the vulnerability will be exploited to materialize a threat by an adversary (internal or external), until such time as it is fully mitigated or remediated.
| Vulnerability | Probability |
| Exploitable | Very likely |
| Identified | Likely |
| Mitigated | Unlikely |
| Remediated | Rare |
CVSS (Common Vulnerability Scoring System SIG) framework provides a method to assess the impact of vulnerability,and As described on the official site, the CVSS SIG methodology allows us to capture the main characteristics of a vulnerability (Base Score), temporality (Temporal Score) and environment (Environmental Score) sequentially, and produce a numerical score (Overall Score), which reflects its severity. CVSS score can be translated into qualitative metrics to simplify understanding and help organizations prioritize vulnerability remediation:
| Score | Severity |
| 0 | None |
| 0,1 – 3,9 | Low |
| 4,0 – 6,9 | Medium |
| 7,0 – 8,9 | High |
| 9,0 – 10,0 | Very High |
While Base Score is mandatory to calculate the CVSS score, it allows optionally to assess temporality and environment. Temporal Metrics have according to CVSS a Remediation Level (RL) component, this remediation level takes into account the following parameters:
- Not defined
- Not available
- In progress
- Temporary Patch
- Official patch
https://www.first.org/cvss/specification-document
The above are remediation states to which weights are attributed, and take into account the state of the vulnerability according to the availability of the security patch corresponding to the vulnerability, and the level of application of the patch, however, the dynamic cybersecurity risk takes into account the state of the vulnerability within its life cycle, within the company’s security processes.
The main reasoning is based on the fact that a vulnerability can have an official patch published, but depend on individual circumstances to each company, not being correctly applied in our infrastructure, only in a percentage of the total number of systems, or not having been applied by some exception.
In the latter case the risk must be treated, accepted or transferred, but it does not cease to exist. Another example would be a security patch that may be in a temporary state, which would be considered as mitigated, but not remediated, so that a security hole still exists. Thus we can determine the Dynamic Cybersecurity Risk by applying the following formula:
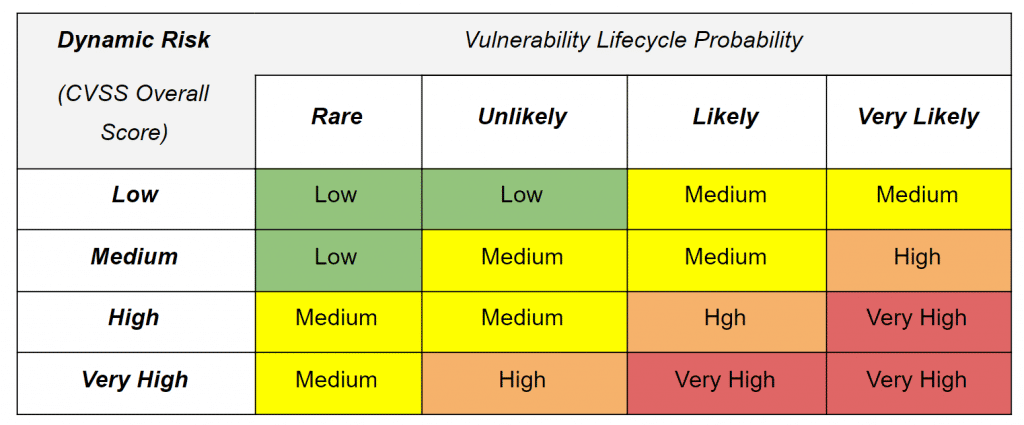
Dynamic Risk (DR) = CVSS Score (impact) * Life Cycle Status (probability).
Making use of the criticality levels defined above both at the level of the vulnerability state within its life cycle, as well as the categorization of the CVSS score qualitatively, the result can be determined by making use of the following qualitative dynamic risk assessment matrix:
With dynamic cybersecurity risks we find a metric that is effective in identifying the impact that existing vulnerabilities con produce over our infrastructures, depending on lifecycle. Then dynamic risk can be associated with a previous vulnerablity prioritization process, which allows us to get a glimpse of the security status of the company.
These results help us to improve different internal processes included in any cybersecurity strategy, security governance and corporate risk management, providing indicators that security management can discuss with the different areas affected.
Discover our work and our Dynamic risk assessment services at www.tarlogic.com
This article is part of a series of articles about Dynamic Risk Assessment
- Introduction to Dynamic Cybersecurity Risk
- Dynamic Cybersecurity Risk Assessment