Introduction to Bluetooth attacks
Table of Contents
Tarlogic starts a series of articles analyzing Bluetooth attacks. In this first installment, we present BIAS and BLESA, two of the threats to the security of wireless devices

In one way or another, Bluetooth is a technology that accompanies us in our daily lives almost without us realizing it. We use it to listen to music, to share information, when working with wireless mice and keyboards or when interacting with smart speakers. Even with other devices that a few years ago would not have seemed implausible, such as a toothbrush or a coffee machine. But what about the security of this technology? The Tarlogic Innovation team will be publishing several articles on Bluetooth attacks in the coming weeks.
The aim? To put the spotlight on a reality that shows some worrying signs.
Before getting to the point, however, a prediction should be made. The ecosystem of Bluetooth-enabled devices is expected to grow significantly in the coming years, especially thanks to the growth of the IoT sector. This is one of the reasons why our team has also developed a Bluetooth LE analyzer to detect Bluetooth devices, called the Acrylic Bluetooth Low Energy Analyzer.
In the near future, in fact, it is very likely that we will be able to interact with countless systems via Bluetooth and other communication protocols.
This first article will introduce some key concepts that are necessary to understand the most frequent Bluetooth attacks, as well as how Bluetooth BIAS and BLESA attacks work.
In the second article of the series, the KNOB and BLURtooth attacks will be presented. Finally, in the third article, the Bluetooth BrakTooth family of attacks will be explained and some final conclusions will be drawn to conclude the series of articles.
So let’s get down to business.
What is Bluetooth?
Bluetooth is a short-range wireless communications protocol used for data exchange between fixed and mobile devices in the ISM bands from 2.402 GHz to 2.48 GHz. As a rule, transmission powers are rather limited (2.5 mW) so the effective signal distance is small (up to 10 m).
Since the Bluetooth 4.0 specification, different Bluetooth modes have emerged. Among these modalities, two stand out: Bluetooth Classic (inherits the existing Bluetooth protocol) and Bluetooth Low Energy (intended to be a low energy communication protocol). These two modalities are the most widespread today and a large part of the devices on the market today support both specifications.
How Bluetooth technology works?
In Bluetooth there are two types of roles, the primary (also called master) and the secondary (also called slave). As a general rule, the secondary device sends advertisement packets and allows another device to connect to it.
The master device is responsible for receiving these advertisements and initiating the connection to the peripheral. It is possible for a device B to play both roles simultaneously, being secondary for a connection to a primary device A and primary for a connection to a secondary device C (see table below). Once communication is established, data is exchanged between the two devices.
| Device A | Device B | Device C |
| Master role (Connection #1) | Slave role (Connection #1) | |
| Master role (Connection #2) | Slave role (Connection #2) |
As an example, suppose we have a Bluetooth headset and we want to connect to the computer. In this case, the headphones will act as peripherals and send packets to the medium informing that they are available for connection. From the computer, these packets will be registered and we will see that the headphones are available for connection. Thus, the pairing or association process will start (if it is the first time we connect), and after finishing, they will connect to the computer (primary device).
How secure is Bluetooth?
While it is true that the Bluetooth standard is updated every year, thus solving the vulnerabilities detected, there are some vulnerabilities that affect a large number of devices since many of them are vulnerable up to BT 5.0 version.
In this series of articles we will briefly present the 4 main current attacks (BIAS, BLESA, KNOB and BLURtooth) and the Braktooth family of vulnerabilities, showing the operation and impact of each case.
1. BIAS: Bluetooth Impersonation AttackS
The BIAS attack, discovered by researchers Daniele Antonioli, Nils Ole Tippenhauer y Kasper Rasmussen, is classified as a MITM attack, so that the attacker listens in and has full control over the communication and can alter it if necessary. The official documentation of the attack can be consulted at the following link BIAS_paper.
It’s important to note that in order to carry out this attack, the attacker does not have to be present during the pairing process of the devices that make up the communication to be attacked.
The attack is based on two specification flaws in the Bluetooth standard up to version 5.0. On the one hand, as established in the standard, when Bluetooth connections are of the Legacy Secure Connections type, authentication between the two devices to be interconnected is not bidirectional, but it is the device in the master role that authenticates the device in the slave role. On the other hand, the Bluetooth standard allows the exchange of roles at any time after baseband paging.
In case the connection is of Secure Connection type, a downgrade to Legacy Secure Connection type connections is forced.
For the explanation of the attack, the following nomenclature will be used to denote the different devices: Alice, Bob and Charlie. Alice and Bob will be the legitimate devices that will form the communication channel that Charlie (the attacker) will try to attack. It will be assumed that in the connection established between Alice and Bob, Alice will take the role of slave while Bob will have the role of master.
When the communication between Alice and Bob is created, these devices will share what is known as the Long term key (LTK), a key from which the session keys used by the devices to encrypt communications between them are derived. Thus, Charlie’s objective (who does not know this key) will be to establish a lawful communication with both devices to perform a MITM attack without knowing the LTK.
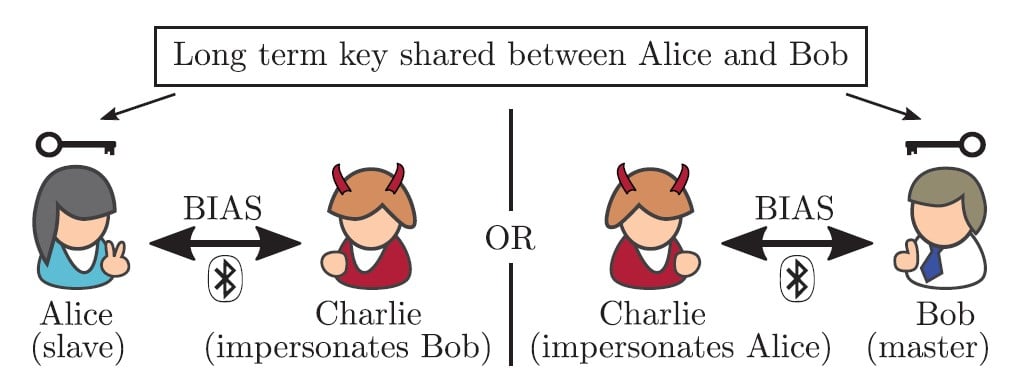
To carry out the attack, the attacker impersonates both Alice and Bob to obtain the necessary credentials to create a MITM. Thus, he simultaneously makes requests to Alice and Bob on behalf of Bob and Alice respectively and, playing with the role changes (authentication is performed only on the master), he is able to perform the attack.
Roughly speaking, the attack execution flow would be as follows.
Charlie forces Alice and Bob to use Legacy Secure Connections.
- Charlie impersonates both devices and makes connection requests to Alice (slave) as Bob (master) and to Bob (master) as Alice (slave).
- Charlie forces the role change in his connection to Bob to be master and thus prevents Bob from authenticating Charlie (impersonating Alice).
- In the negotiation phase Charlie reflects the necessary packets (random number) to establish the session key between Alice and Bob.
- After the session key is established, the attack is completed and all communications go through Charlie.
In the case where it is not possible to downgrade from Secure Connections to Legacy Connections it is also possible to perform the attack although it requires some additional steps as packets with random numbers are exchanged in both directions of communication. Otherwise, the attack is similar to the one presented.
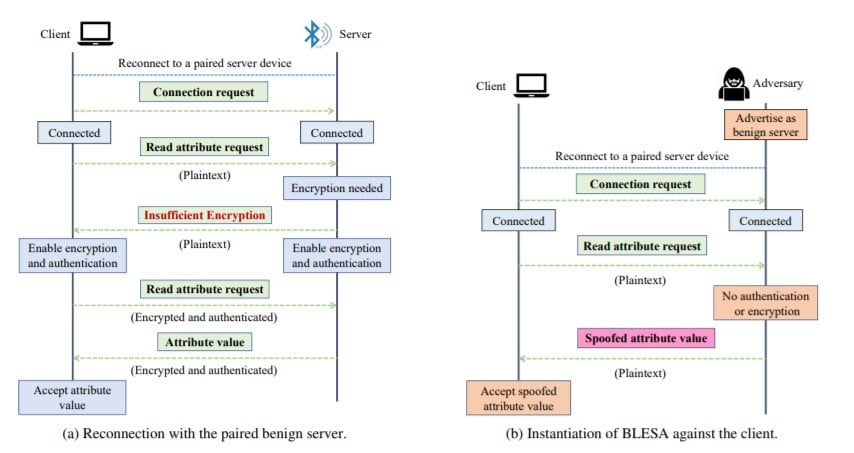
2. BLESA: Bluetooth Low Energy Spoofing Attacks
This attack discovered by researchers Jianliang Wu, Yuhong Nan, Vireshwar Kumar, Dave (Jing) Tian, Antonio Bianchi and Dongyan Xu (Purdue University) and Mathias (EPFL) is valid only for devices running Bluetooth Low Energy. The official documentation of the attack is available at the following link: BLESA_paper.
The attack is based on impersonating the device acting as a server in order to use the different Bluetooth security levels to access different attributes and falsify data. The impersonation is always performed by forcing reconnection with the legitimate device to be attacked.
The impact of this type of attack is highly conditioned by the context in which it is used. An example of the use of this type of attack can be to disable a device by falsifying the battery level and forcing a security shutdown.
After presenting BIAS and BLESA, the next article of the series will explain how KNOB and BLURtooth attacks work and their impack.
References
● Antonioli, D., Tippenhauer, N. O., & Rasmussen, K. (2020, May). BIAS: bluetooth impersonation attacks. In 2020 IEEE Symposium on Security and Privacy (SP) (pp. 549-562). IEEE.
● Wu, J., Nan, Y., Kumar, V., Tian, D. J., Bianchi, A., Payer, M., & Xu, D. (2020). {BLESA}: Spoofing Attacks against Reconnections in Bluetooth Low Energy. In 14th {USENIX} Workshop on Offensive Technologies ({WOOT} 20).
Discover our work and cybersecurity services at www.tarlogic.com
This article is part of a series of articles about Bluetooth attacks