Hardening of Windows systems: network authentication
Having professionals trained and involved with system hardening offers the possibility of having secure implementations and avoids misconfigurations

Systems hardening requires dedication. And knowledge. An essential combination to overcome the bad configuration that we have found so many times in companies.
A bad configuration that is far from new. Go ahead, this article doesn’t try to discover the wheel. In fact, we will talk about using tools that other people have already developed, so the credit is not mine.
This time, we want to focus on the use of RDP. A utility that all sysadmin use every day but that, due to different cases, isn’t well configured on many times.
A very common environment is that of the company that for more than five years had obsolete equipment (XP, 2003 for example, which did not have the option of network authentication prior to RDP (NLA)) on its network. And these coexisted with more modern operating systems: W7, W10, W2012…
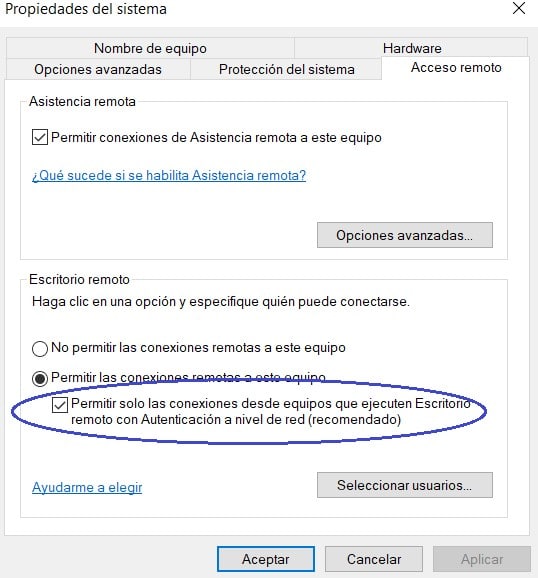
In these environments, the default way to connect to their computers via RDP was not to have an option enabled that in Windows 10 is enabled by default. This is Network Authentication for RDP (NLA):
This option requires the user connecting via RDP to authenticate securely before establishing a session with the server. This minimizes DOS attacks, allows single sign-on, and mitigates RDP vulnerabilities. All are advantages.
There are different attacks on the RDP protocol, such as the well-known Bluekeep, and in the future there will surely be many others.
In this article we are going to analyze the picaresque of using public tools like Seth, which help us carry out an MITM-type attack to get the credentials of users that use RDP. For example, a Sysadmin that occasionally connects to the company’s DC.
Let us assume the following scenario. A malicious user or an insider wants to get valid Sysadmin credentials.
The malicious user or insider performs preliminary discovery tasks to determine which machines to attack. To do this, he needs to know the IP of the DC and the IP of the Sysadmin machine. It will do this with nmap, netdiscover … even with the use of social engineering.
The insider could even force the blocking of different user accounts to generate incidents within the company itself to force the Sysadmin to connect to the DC to see the status of the accounts.
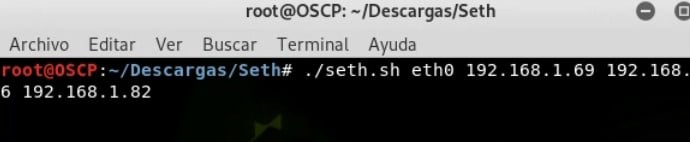
On a Linux machine it makes use of the Seth tool, simply passing the following arguments:
● Network interface to use.
● Attacking machine IP.
● Sysadmin machine ip.
● Target machine IP (DC).
https://github.com/SySS-Research/Seth
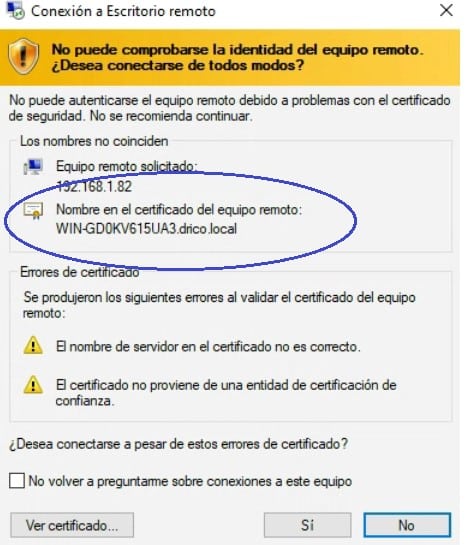
Poisoning at the network level occurs. And also a CREDSSP downgrade is made, a forged certificate is presented, so that the Sysadmin will enter its credentials and accept the certificate (the issuer is apparently the DC itself):
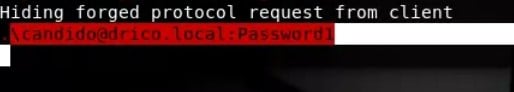
The moment the Sysadmin accepts it, the attacker obtains the credentials in clear text … At that point, all the details of the certificate should be analyzed in order to verify it, but … Does any Sysadmin do it?
And now it only remains to find the right moment to do magic with RDP itself or other tools such as CrackMapExec, PStools … Here the imagination is free.
The conclusions
It is important to highlight the importance of knowing the different options for system hardening and security that Windows offers.
When an option tells us about authentication, encryption … before disabling it without thinking we must investigate the implications and analyze the possible risks. In the case of RDP, without going any further, there are many.
The updates that the manufacturer offers or the default security settings represent another important variable to consider. As well as not using protocols or characteristics of the same that are obsolete, as is the case with RDP.
Having personnel involved and dedicated to the hardening systems as a continuous task offers the possibility of having secure implementations. A very valuable asset within cybersecurity services.
Also the ability to detect unsafe or erroneous configurations. Providing the company with more secure and reliable systems, avoiding present and future threats.But the worst thing that can happen in a company is having conformist Sysadmins.
Professionals who only care that things work. But they don’t really know how they work. Professionals who, in their day to day, endorse that saying of the wise man:
What is worse, ignorance or not know?
You judge.
Discover our cybersecurity services and our system hardening services