DSL Communications Interception – TR069 – Part 4
We continue with the analysis of DSL routers security and communications interception (See previous Part I, Part II and Part III).
After having correctly configured our DSL infrastructure, we can start analyzing the TR-069 management protocol . This protocol is a sequence of SOAP messages over HTTP, with an optional encryption layer.
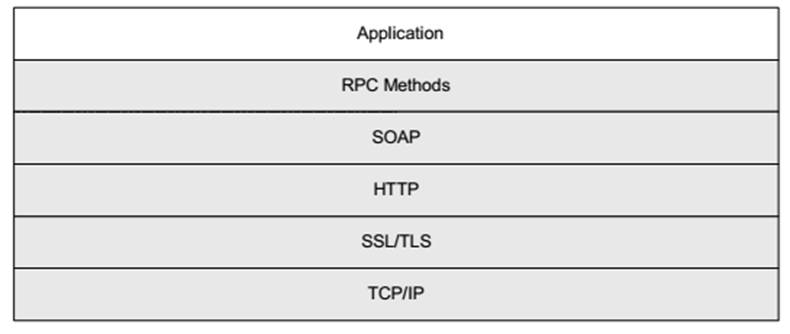
In case it is not immediately obvious, an ACS is the complete owner of an ISP’s entire router infrastructure as it can force virtually any action on them. The ACS URL, to which the CPE connects, can be set or modified in the CPE through several mechanisms:
- At the firmware that comes pre-installed on the device.
- Locally via TR-064, web interface, telnet or ssh.
- From the ACS itself through the TR-069 protocol.
- Through DHCP through option 43 (provided that it has not been previously configured).
Typically, the connection between the CPE and the server is encrypted via HTTPS. For additional security, the communication is encrypted with an SSL certificate stored in the router or cable modem itself. It is therefore necessary to extract the SSL certificate from the firmware of an ISP’s router beforehand in order to establish SSL connections with the ISP.
In order to fully capture the generated management generated traffic we would perform an SSLstrip style attack, configuring the router to connect to the ACS via HTTP while we perform a MITM redirecting the traffic against the SSL service of the ACS. At this point we would have an unencrypted capture.
What we would be seeing with a connection to the ACS over HTTP, or with the MITM, would be as follows:
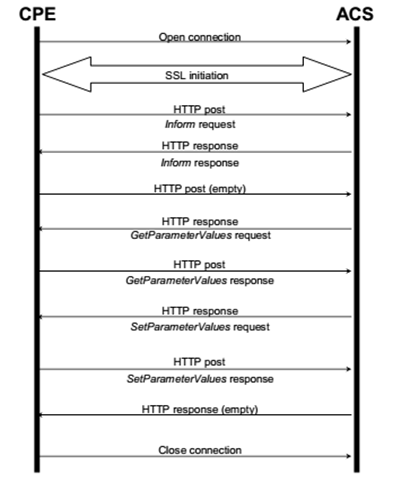
The connection against the ACS is always initiated by the CPE by sending a TR-069 inform message. After exchanging information between them, the CPE remains inactive for a period of time until it will re-establish the connection to exchange information again.
The ACS may also establish connections directly against the CPE to send it information or to instruct it to connect against the ACS. To do this it must access a specific URL of the CPE which normally requires Digest authentication (MD5).
The username always follows the scheme:
- <OUI>-<ProductClass>-<SerialNumber>
- <OUI>-<SerialNumber>
As a curiosity, the connection between the CPE and the ACS is made over HTTP, with no encryption.
Discover our work and cybersecurity services at www.tarlogic.com
This article is part of a series of articles about DSL Communications eavesdropping
- DSL Communications Interception – Introduction – Part 1
- Interception of DSL Communications – Synchronization – Part 2
- DSL Communications Interception – Administration – part 3
- DSL Communications Interception – TR069 – Part 4
