TARLOGIC's BLOG
Cybersecurity - Page 13
Cybersecurity articles with security analysis and ethical hacking technics information

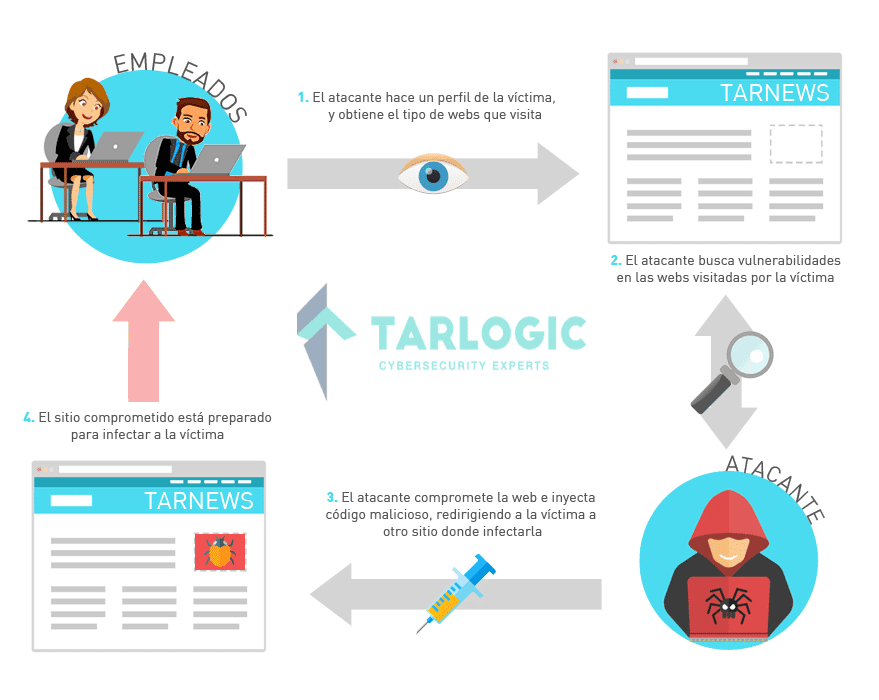
Same-Site cookies against CSRF attacks analysis
CSRF vulnerabilities Cross-site request forgery (CSRF) vulnerabilities are extremely common in web applications. Despite they are known since a long time ago, we are used to find t[...]
Read more
How PHP Object Injection works
PHP Object Injection enables the arbitrary manipulation of an object content that shall be unserialized using the PHP unserialize() function. This kind of web application vulnerabi[...]
Read more
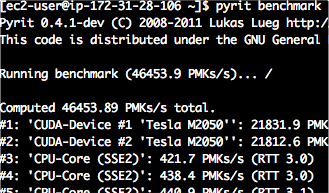
Enterprise WiFi network security audit from openwrt
The main difficulties found when performing a security audit of Enterprise WiFi network by a security analyst in ethical hacking are the following: WPA Enterprise networks imperson[...]
Read more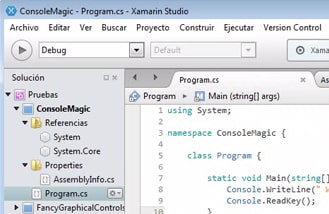
Backdoors in IDEs – RootedCON 2015 Talk
This article describes in detail the content of “Bend the developers to your will” talk given by Miguel Tarascó and included in RoodCON 2015 Congress. 1. Why developers? Devel[...]
Read more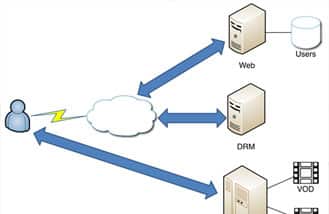
Platform in the Middle – Bypass DRM protections at Content Delivery Networks
Please find below the description of the research about Platform in the Middle attacks carried out by Tarlogic and included in RootedCON 2015 congress. These attacks refer to Inter[...]
Read more