
TARLOGIC's BLOG
Cyber Intelligence
Mitigating business risks and threats with cyber intelligence.
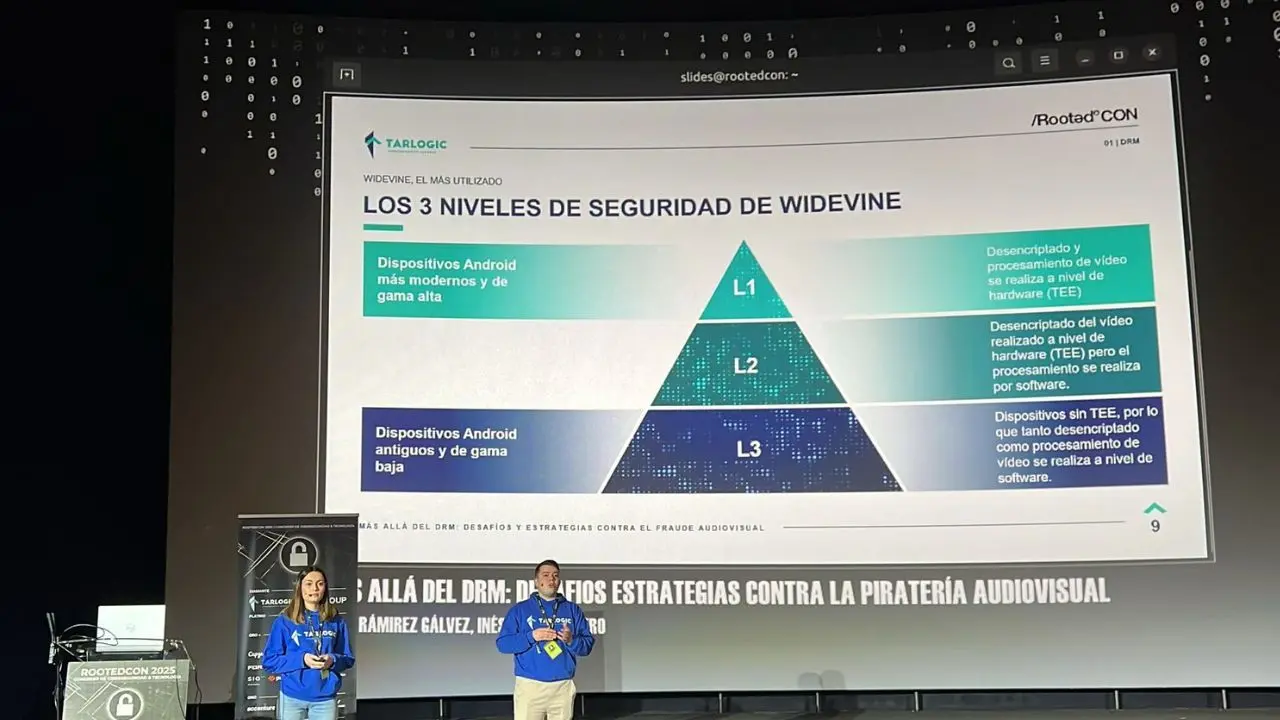
Fight against audiovisual piracy, the challenges
Combating audiovisual piracy requires continuous investigation into fraudulent activities and the optimization of mechanisms to prevent, detect and respond to them Almost one in tw[...]
Read more
SIM swapping, when your phone, and your money, are out in the open
SIM swapping fraud, the lawless duplication of a cell phone card to impersonate a person’s identity, is growing. As a result, operators and banks are already reinforcing thei[...]
Read more
Hacking of social network accounts and creation of fake profiles: No one is safe
Social networks are fully incorporated into our lives. Currently, 85% of the Spanish population uses a social network, both on a purely personal and professional level. Likewise, 6[...]
Read more
Stolen accounts, IPTV apps and pirate platforms: how audiovisual fraud work
You get home after a long day at work. You open a bottle of wine and sit down in front of the TV to watch an episode of a series that helps you relax and disconnect. But when you t[...]
Read more
Counter-Phishing: Anticipating the criminals
Generally speaking, we estimate risks based on our ability to protect ourselves against the actions that trigger them. This capacity increases the more knowledge we have of the eve[...]
Read more
Getting up before you fall: how to manage a cyber crisis
Cyber crisis management requires constant updating of knowledge due to the characteristics of the Internet[...]
Read more
The secretary who loved cyberintelligence
Anticipating to competitors, contain data leaks, prevent fraud. Cyberintelligence services applications will be crucial for businesses in digital age A seemingly minor variable. An[...]
Read more
CDS. Corporate Digital Surveillance. Advanced Business Protection
Many professionals assume that a permanent state of ‘total cyber security’, with a continuous 100% protection guarantee, is impossible. Therefore, the effort must be directed t[...]
Read more
Teleworking and Insider Threat. New opportunities for an old acquaintance
Julian works in the sales department of an automotive components company and has good business relationships with distributors and suppliers in the sector. In the past, he has on o[...]
Read more
Data Collection Plan: A Key Component of the Intelligence Cycle
Data collection is a major step in the intelligence cycle, as it involves gathering the information to be used in other stages of the process and delivering the intelligence produc[...]
Read more