Backdoors in IDEs – RootedCON 2015 Talk
Table of Contents
This article describes in detail the content of “Bend the developers to your will” talk given by Miguel Tarascó and included in RoodCON 2015 Congress.
1. Why developers?
Developers are an infection vector and a very interesting entry point in companies since they are usually privileged users having access to configuration credentials or files. In many cases, they hold production servers access and as they are humans, they need to look for information or “inspiration” on the Internet.
2. Objectives.
The main aim of the talk is not tackling how to infect code, but stepping backwards in order to have an overview of a developer daily routine. Then, we are going to analyze which tools developers use and which ones can be forced or abused in order to make the developer carry out non-defined or non-expected tasks which could be used to deploy backdoors from the code and enable arbitrary command execution or system infection with malware.
3. State of the art
Code trojanization and backdoors hiding is nothing new. It has been always done by using application source code hiding calls or using malware infecting source files after a non-authorized access. The clearest case is malware attacking web servers in order to embed calls to an exploit kit or iframe to finally carry out clients’ attacks.
4. Compilation managers backdoors
Development projects are complex and a big number of developers are involved. Therefore, compilation managers have appeared in order to ease the management process. They are responsible for managing those files to be compiled as well as organizing the order that the process should follow to avoid problems in tasks.
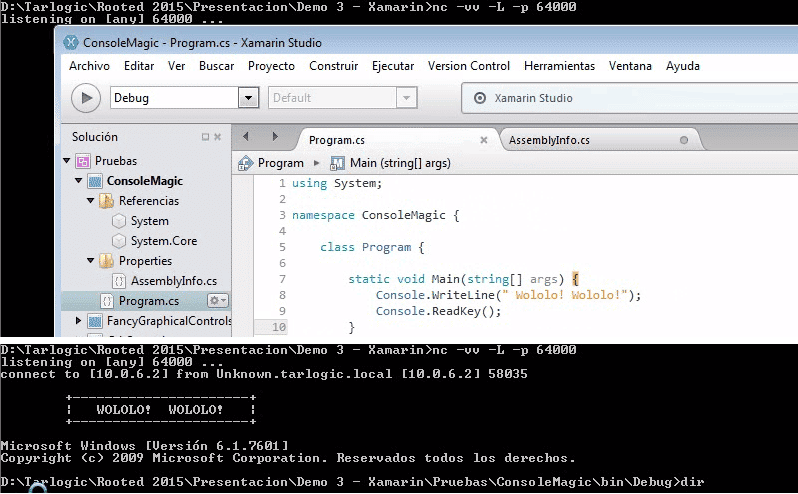
For this talk, make compilation files were examined. This process fulfillment can be observed from the Visual Studio with MSBuild and Gradle (used in Android Studio) and also with Xamarin (previously called MonoDevelop). This is a cross-platform IDE for Windows, MacOsx and Linux compatible with .Net using Mono.
Please, find below the links corresponding to the first three demos tackling backdoors running in the following platforms:
- Demo 1: MsBuild
- Demo2: Gradle in Android Studio
- Demo3: Xamarin
Please observe here how to abuse of these managers and how it is possible to insert a backdoor in the system only compiling the code without need of running the result and do a “Man in the middle” to the compiler inserting a code backdoor in the resulting binary as well as command execution or file writing, as malware or APTs.
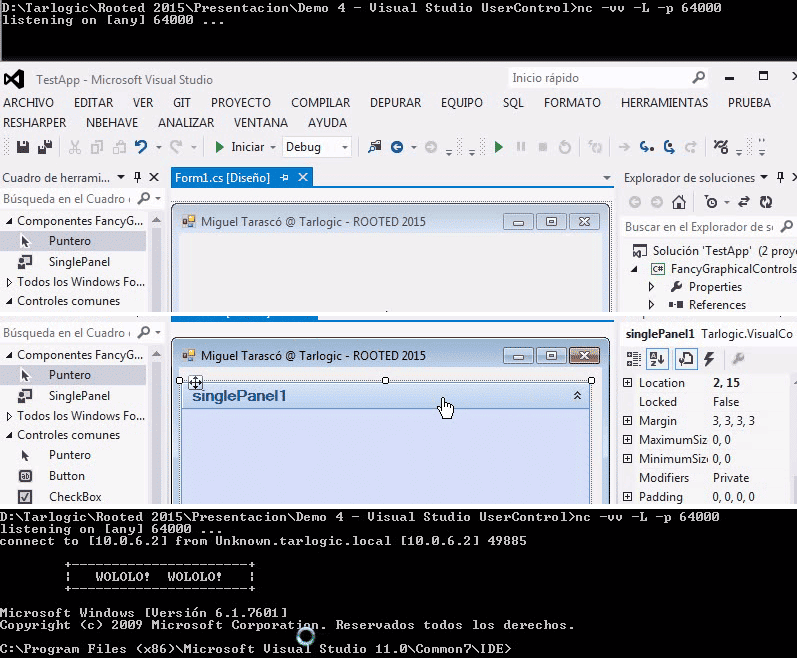
Yet another step has been taken in order to overview an application development therefore, it is analyzed what is happening during graphical application development and also, how these applications use graphic components during design time. It is also shown, what they are and how they can be designed by a developer in order to adjust the desired shape and behavior.
From Visual Studio, it will be checked what is happening when including a graphic component to any form and also how the code is executed only mousing over and therefore enabling system trojanization or arbitrary commands execution. This happens due to the way IDEs provide the possibility of drawing components in design time as well as interacting with them from the designer. Besides, a test will also be carried out with Android Studio in order to check behavior when managing graphic components.
Please find demo video available here.
5. Conclusions
The conclusion to be drawn after this study is that we cannot trust source code published on the Internet, even though we are not running it since it can include backdoors that may run during the design or compilation time.
Due to all this we should never trust on code developed by strangers, therefore we should always check the source code and also the rest of project files and use always code from virtual machines or sandboxes in order to avoid development systems infection with backdoors.
Discover our work and cybersecurity services at www.tarlogic.com