randomHeader extension for burp suite
When performing a web application security assessment that has the capability to detect and block attacks, the auditor has to figure out how to successfully complete the audit when these security elements block the client’s IP address.
Depending on how the application is configured and depending on the different perimetetral security elements that are part of the network architecture, the manipulation of the source IP address, through HTTP headers, can be enough to defeat the protection mechanisms. For example, a misconfigured application can make use of HTTP headers such as X-Forwarded-For to trigger actions against the client. Improper handling these IP addresses, sometimes manipulable by the user, can lead to the following:
- Bypass IP blocking when an attack occurs.
- Block another legitimate user.
- Block infrastructure IP addresses.
- Perform brute force attacks against authentication modules.
- Successfully complete tests from automated tools.
In order to automate this process we have created a new burp extension called randomheader that allows us to automate this process by generating, in each request, a set of fake HTTP headers in which a random client IP address is provided.
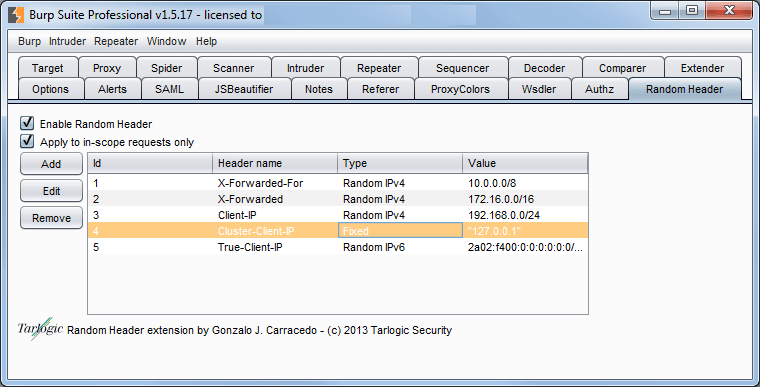
This burp extension allows to generate random HTTP headers on each request, both for IPv4 and IPv6 addresses, as well as for values retrieved from a file.
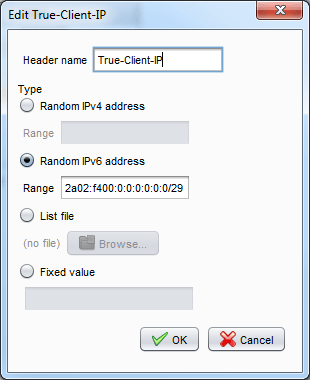
Let’s consider the case of a website published through a CDN like Akamai. On every request that a client places, the CDN delivers that request to the company’s edge network, with an additional HTTP header that contains the user’s real IP address.
If the web platform does not restrict incoming connections from the CDN nodes, or attempts to obtain the client’s real IP address from HTTP headers, it could be possible for an attacker to connect directly against the web platform and send spoofed and random HTTP headers, evading blocking and protections against brute force attacks. Examples of HTTP headers that could be triggered from the randomHeader module:
- Client-IP
- X-Forwared-For
- TRUE-CLIENT-IP
- HTTP_CLIENT_IP
- HTTP_X_FORWARDED_FOR
- HTTP_X_FORWARDED
- HTTP_X_CLUSTER_CLIENT_IP
- HTTP_FORWARDED_FOR
- HTTP_FORWARDED
The following is a standard HTTP request launched from the burp repeater module:
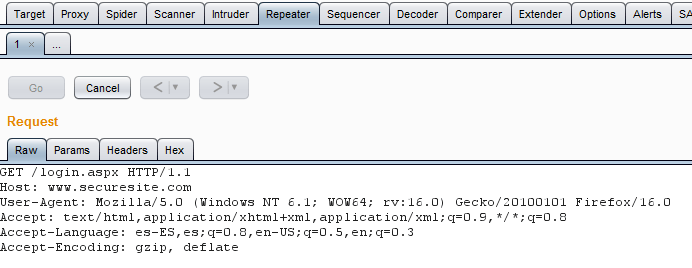
Automatically and transparently for the user, the randomIP extension generates new headers to be sent to the web server.
We hope you find it useful. You can download both the source code and the Jar module at the following link: randomIp burp suite extension
Discover our work and cybersecurity services at www.tarlogic.com
