Interception of DSL Communications – Synchronization – Part 2
We continue with the articles on DSL router security analysis and communications interception (See Part I).
When the investigation of several communication devices started, only the users’ routers were available, so it was Tarlogic’s task to set up its own DSL infrastructure in order to analyze both the risks faced through the ISP and its subscribers.
Once the DSLAM was in the hardware security lab, the first thing that had to be done was to assemble a cable to connect the routers, via its RJ11 port, to the RJ21 interface of the DSLAM. This cable can also be purchased on the Internet for about 50€.
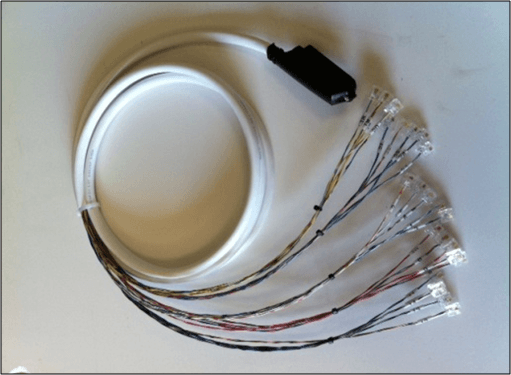
Cable de RJ11 a RJ21
The ultimate goal was to setup two of the most used modes nowadays by the main Spanish operators: PPPoE and IP over Atm (IPoA), so once the DSLAM was connected to the routers we proceeded to implement the next task, configure the DSLAM and the additional services needed for the ADSL infrastructure to be fully operational in both modes.
The main parameters to be configured in the DSLAM, which can be extrapolated to a router with an atm interface, are the VPI (Virtual Path Identifier) and VCI (Virtual Channel Identifier) of the ATM channel (PVC) and a default route so that this device knows where to send the data received from the users’ routers.
- PPPoE (PPP over Ethernet)
Este protocolo, cuyas bases son descritas en el RFC 2516, permite implementar una capa IP sobre una conexión entre dos extremos Ethernet. En la siguiente tabla podemos ver la arquitectura de una red de este tipo.
[table id=1 /]
Among its advantages are that it allows encryption, authentication and compression of the transmitted data.
For this connection mode, in addition to the DSLAM, it was necessary to configure a PPPoE server that would be the end point of the PPPoE tunnel and would also allow assigning an IP address to the router and authenticate users, performing the function of what in the first article of this series we identified as BRAS (Broadband Remote Access Server).
The edited files were pppoe-server-options and pap-secrets (both are normally found in /etc/ppp) and a new file was also created, called pullips, where the range of IP addresses that the server would assign to the routers was indicated.
Once the previous steps had been completed, the only thing left to do was to run the service indicating the interface through which the requests would be received.
- IPoA
This connection mode is described in RFC 1932
In addition to the DSLAM configuration, for the correct operation of this mode, it has been necessary to configure a DCHP server whose function would be to assign the IP address to the users’ routers.
To configure the DCHP service it was only necessary to edit the dhcpd.conf file, which is normally located in /etc/dhcp as follows:
subnet 192.168.1.0 netmask 255.255.255.0 {
range 192.168.1.11 192.168.1.29;option domain-name-servers 192.168.1.1, 193.146.96.2, 193.146.96.3;
option domain-name “tarlogiclab.local”;
option routers 192.168.1.1;
option subnet-mask 255.255.255.0;
option broadcast-address 192.168.1.255;host router1{
hardware ethernet 12:12:12:12:12:12;
fixed-address 192.168.1.11;
}default-lease-time 86400;
max-lease-time 172800;
As can be seen in the previous example, in our case we used a static assignment based on the physical address of the routers.
Once the configuration of these services was completed, we had routers with IP addresses with Internet access and a topology similar to the one shown below.
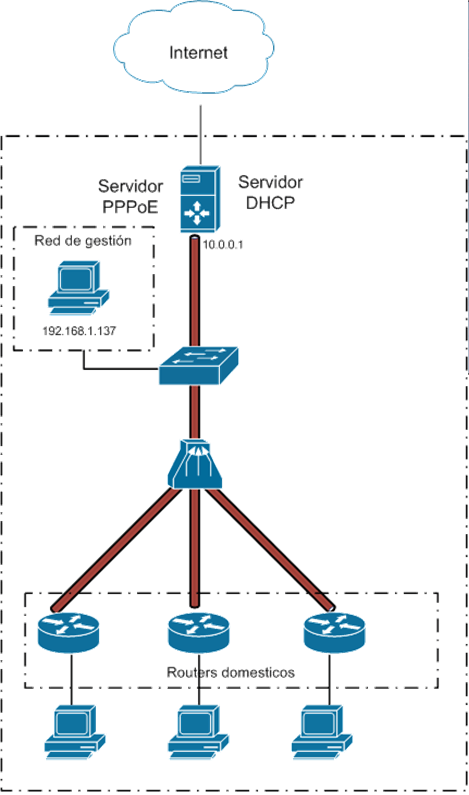
Topología de red DSL básica
A basic and functional DSL infrastructure is now in place. Any equipment connected to the LAN side of the DSL routers will be able to navigate through the Internet, exiting through the DSLAM laboratory.
The managed switch will allow, through the use of port mirroring, the interception and initial analysis of communications and their integration with a monitoring and attack detection system.
Discover our work and cybersecurity services at www.tarlogic.com
This article is part of a series of articles about DSL Communications eavesdropping
- DSL Communications Interception – Introduction – Part 1
- Interception of DSL Communications – Synchronization – Part 2
- DSL Communications Interception – Administration – part 3
- DSL Communications Interception – TR069 – Part 4
