Hybrid Threats against Companies
Table of Contents
Hybrid threats are not new to the corporate sector
Expressions such as hybrid war and hybrid threat have given name to phenomena of increasing prominence so far this century. At the same time, the definition of notions behind those terms has been progressively narrowed. There is also a growing effort to better understand and study this concern.
Term and concept correlation was originally developed in the military and geopolitical domains, as a result of new ways of understanding war, changes and developments in national strategies and confrontation between countries. The term hybrid refers to a state of non-direct, latent conflict which does not openly and officially escalate beyond certain limits, and where casualties and/or direct damages are not agreed upon by the parties.
In the past, war was officially declared or began in an overt and direct way, after a sequence of events. The term hybrid is used today to refer to the indefinite period in which conflict already exists though it is not yet recognized, extending over time without a clear beginning or end, and where actors involved avoid establishing attribution or claiming any action and, in some cases, even deny having been attacked.
The above reflects the scenario in the military and geopolitical domains, but the economic field, particularly the business and corporate environments, shows a different situation. Companies have always been exposed to what is now called hybrid threats. However, unlike military confrontations, there cannot be, strictly speaking, enemies in the business sector, since competitors cannot be physically destroyed or annihilated by applying direct methods. Instead, there are firms that experience intense competition and mutually recognize each other as rivals, which might lead to an escalation of companies’ rivalry persisting over time.
There are rivals that compete against each other in a permanent and evolving way, although they can also undertake joint projects or build alliances of different nature (as temporary business associations, consortiums, etc.). The dynamics of companies’ relationships undergo constant changes, allowing them sometimes to share interests in the short-term, but with a scope and duration hard to predict. In fact, two or more companies can even engage in coopetition at the same time, though in different scenarios. 21st century businesses team up with coopetitors, a buzzword becoming increasingly accepted in the international corporate sector to describe cooperating competitors.
Company rivalry is not regulated by a law of war imposing limits and restrictions. On the contrary, competitors are governed by market law and the same codes of practice applied to the whole of society and adopted in international relations. Hostile actions conducted in this market and competition oriented ecosystem are then considered to be of hybrid nature, given the fact that these actions are covert, aim at specific targets and are difficult to attribute.
In this game, states operate as actors in support of their national companies, triggering the effect, scope and consequences of implemented hybrid actions. It is not uncommon today for companies to compete with rivals backed up with government resources, either of economic, political, diplomatic, intelligence or soft power nature.
Competitors, states and other actors
Besides competitors and states supporting their national companies, the universe of potential hybrid attackers is also composed of other actors operating autonomously outside public and corporate structures.
Despite these being smaller scale actors, they are highly specialized. They have developed the knowledge and skills required to launch an attack and carefully study the targets being considered. Their actions can be either sponsored or carried out independently, and can efficiently meet the targets set. When compared to terrorist attackers, individual actors are considered to be the lone wolves of business hybrid threats. They perform their activities either on a professional or amateur basis and get involved in cyberspace as hacktivists, attackers of occasional fortune or attackers driven by different motivations.
Other actors have a broader range of action. They can participate in the design or performance of a hybrid action or threat against a company, either in a conscious or unconscious way. When they act in an unconscious way, they are steered or manipulated by others, as is the case for journalists, social communication media, trade unions, NGOs and other social and civic associations linked to the business sector.
Furthermore, relations with clients and providers are not always easy for companies. A variety of disagreements, differences and other issues may arise within the contract period. Consequently, clients and providers can also be the source of hybrid threats affecting a company.
Finally, it should be borne in mind that a company being disrupted might not be the ultimate target of the attack, but a stepping stone chosen for a number of reasons. For instance, to send a clear message to the state where the company is based or because that company is a key link in the supply chain, and when this is broken down, the corporation remains seriously affected, which is the real objective of the hybrid operation.
Globalization and digitalization
Globalization and digitalization are clearly determining the way we all relate to each other: people, states, companies… The above two factors are also shaping our perception of the risks and threats existing in the business sector, giving the feeling that these are new or recently emerged challenges.
However, many of these threats are not new, though they have now become widespread and available for actors to develop. This is caused, on the one hand, by market globalization, understood as internationalization and integration of markets despite occasional protectionist measures or trends, and on the other hand, by progressive digitalization of economy. As a result, hybrid actions carried out in the business field are now very affordable and show a seemingly high profitability. In fact, any potential attacker willing to disrupt a particular company can have a great impact at low cost, even when sophisticated resources are not available.
Globalization has turned the whole world into a single scenario in which to compete. Companies can now sell their products, expand their business and develop their activities in any place of the world. Accordingly, exposure of companies to risks and threats has dramatically increased, as is the potential source of those risks and threats, which can be located anywhere in the world.
Digitalization of economy has boosted the profitability of hybrid threats for attackers. Low-cost actions can result in huge company losses, whether in financial, technological or reputational terms. Besides being cost-effective, many of these actions are easy to deploy because of their digital source, which does not require using neither complex or permanent infrastructure nor dedicated human resources. In addition, efficiency of these threats is considered to be that high as effects are noticed soon after the action is launched.
Two other features make hybrid threats even more appealing to potential attackers. Firstly, actions are virtually anonymous, as these are hard to backtrack and attribute. Secondly, actions are very reactive, taking into account the multiplier effect they have through digital social networks and social communication media.
Thus, globalization and digitalization have broadened the scale of threats against any business organization or corporation, at the same time that these actions are more profitable than ever. In addition, the number of actors that might be involved, either actually or potentially, in hybrid actions has ramped up. There is no company deemed to be considered free of risk, nor acknowledging the full list of risks, threats and potential attackers.
Company threats are spherical and fast-evolving, in the same way that market, competitors and providers, alliances and partners, regulations and standards are constantly changing.
Targets and Scale
The main motivation behind hybrid aggressions in the business field is always of economic nature. Even when it is very difficult—if not impossible—to attribute and backtrack a hybrid attack, it is highly recommended to examine the reasons and plausible assumptions explaining the cause of the aggression. This allows to short-listing the most likely attackers, while identifying those benefiting the most from this action.
As stated before, the main motivation is of economic nature, but it is important to remark that this is not the only motivation, as hybrid aggressions against companies may have geopolitical derivatives in terms of symbology and conflict between states and/or blocks and may also be the outcome of personal rivalry in firm competition.
After a hybrid attack, companies do not only experience loss of competitiveness and weakening of corporate governance, but they also have to address competitive advantage of rival firms. Furthermore, these activities can cause collateral economic damage and inadvertently affect other actors. In this respect, it is necessary to recall that attacks can have an indirect approach and the disrupted company may not be the ultimate target, but the means to the end as it can act as a key player—either as a provider, partner, client, consultant, etc.—for the target entity.
Taking into account that aggressors seek to gain competitive advantage, hybrid actions are designed to disrupt the most critical parts of the targeted organization, and when not possible, to address the most vulnerable elements and then progressively escalate to critical parts. The sequence of actions to be taken is as follows: Vulnerability – Persistent Hybrid Influence – Threat – Hybrid Action.
Once a business vulnerability or security breach is identified, influence campaigns consisting on a number of actions, more or less persistent, are generally run. Under these campaigns, fake news or propaganda is spread, information is disclosed and/or leaked through social networks and social communication media—manipulated either in a conscious or unconscious way—and personnel, product or service data are disseminated with a view to weaken the attacked company. The escalation of confrontation levels can occur sequentially or simultaneously, and it may include direct physical attacks (such as theft, sabotage, protest actions, etc.), cyberattacks (against databases or critical infrastructure, through data exfiltration techniques…) or combined attacks (such as an insider threat). At a later stage, third parties might be involved after being manipulated of forced knowingly or not, as is the case of NGOs, banks, public institutions, politicians or administration services that will eventually adopt social, financial or regulatory initiatives, among others. Initiatives such as these will impose pressure and undue interference to the corporate governance of the company under attack.
In short, the ultimate target of hybrid aggressions is to gain competitive advantage. The attack will address the most critical and/or vulnerable parts of the corporate organization. Escalation of hybrid actions will occur either sequentially or simultaneously insofar planned targets are achieved.
Management and response: The value of intelligence
A scenario where companies are exposed to a higher number of risks and threats difficult to identify, define and address was described so far. However, the fact that hybrid threats and risks are covert and hard to backtrack does not mean that they are impossible to tackle. Companies are not fully unprotected nor completely vulnerable against hybrid threats, as higher exposure does not entail powerlessness.
Companies need to implement measures to reinforce their security against hybrid threats in a realistic manner, that is to say, taking into account that security is a constantly changing process, instead of a static scenario, and assuming that no matter what companies do, they will never be 100% secure. And because full and permanent security does not exist, it is not possible to guarantee maximum security for companies (100% secure, 24/24).
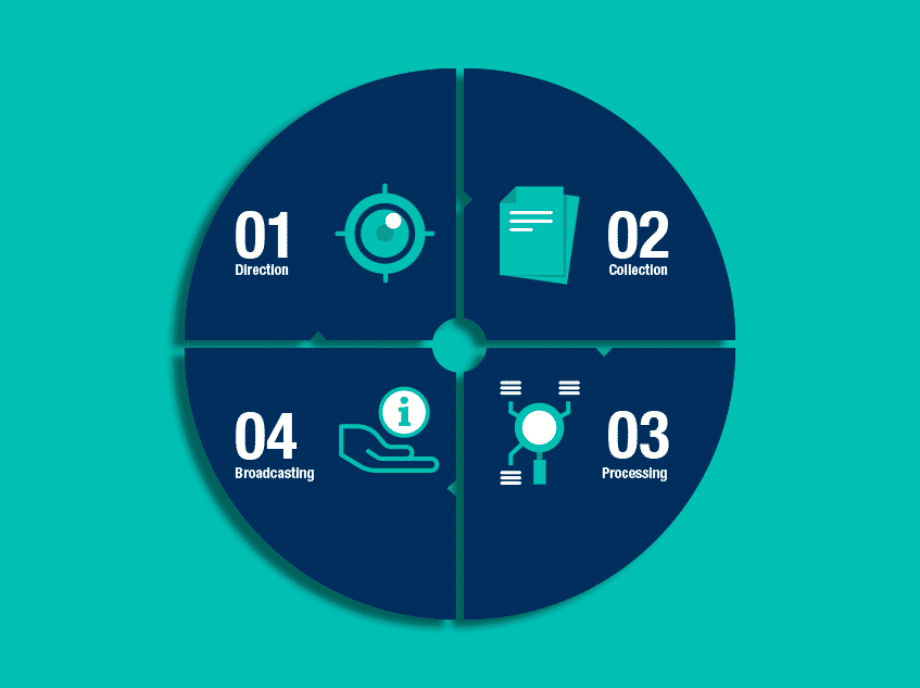
What companies need to do is to properly assess the level of hybrid threats they are exposed to, outline a range of plausible scenarios where such threats can arise and develop response actions to contain any potential attack. When securing companies against hybrid threats, the role of intelligence is of utmost relevance. In the business domain, intelligence translates into security based on business continuity for the organization. To this end, relevant corporate departments need to contribute with their capabilities to this common effort.
By using tactics, techniques and procedures (TTPs) for intelligence operation, companies can anticipate a hybrid threat or risk while it is still in the planning stage. This stage involves a high cost for attackers, as they need to gather any relevant information to identify vulnerable and/or critical parts of target entities and this requires much dedication. In this sense, corporate use of intelligence has a valuable deterrent effect.
It important to highlight that many hybrid threats become real after the execution of minor individual and independent actions. Such minor actions are usually of hybrid nature and are apparently harmless when considered individually, but very harmful when operated sequentially. The high value of intelligence is also revealed when tackling minor hybrid actions, which are more difficult to identify and are seldom regarded as individual parts of a more sophisticated aggression.
Because of the digital nature of most hybrid threats against companies, cyber intelligence has proved to be the most efficient resource to identify, understand and neutralize them. Most companies resort progressively to specialized services in cyber intelligence and control risk to cover other aspects of corporate security in the organization, such as promoting staff awareness and checking and improving business continuity plans.
Sum of capabilities: Deterrence, containment and response
Though it cannot yet be qualified as doctrine, there is a growing consensus among experts and professionals that the best security scheme to counter hybrid threats needs to be based on public-private cooperation, with seamless exchange of information and commitment of all participants to contribute with their capabilities.
This collaboration principle is included in a growing number of security and cyber security strategies implemented by states and supranational organizations, and is especially applicable to companies and corporate organizations that are exposed to hybrid risks and threats.
Companies’ security plans are the first step of defense to counter potential hybrid threats. Those plans have to refer to the specific defense needs to be outsourced to specialized security and intelligence companies and consultancy firms. These capabilities are the second step of defense and help to respond to alert situations or certain scenarios foreseen in companies’ security plans. In addition, companies can get profit of enhanced capabilities provided by public organizations involved in safeguarding the security and cyber security of states and supranational organizations. This represents the third step of defense, which is especially useful for strategic companies, i.e. organizations operating in key sectors of economy, having a high technological value that need to be protected or acting as critical providers for the state administration.
Concentration and integration of internal, external and public security and intelligence capabilities assures the best integral security system for companies to counter hybrid threats and risks, as it deals with deterrence, containment, neutralization and even response. Regarding the latter, it is important to mention that the discussion on allowing hack-back actions, regarded as a legitimate offensive action in response to an aggression, has gained steam in recent times.
Implementing an integral security scheme such as the one proposed in this paper contributes to building a community of trust where not only companies are being benefited. Consultancy firms, security companies and public organizations can also be enriched with knowledge and experience gained from the fight against hybrid threats.
Conclusions
Companies have always been exposed to hybrid threats and will continue to be so in the future. Globalization and digitalization of economy contribute to maintain this situation and force companies to pay particular attention to cyberthreats.
Despite being increasingly exposed, companies are neither defenseless nor unprotected against hybrid threats. Threats can be identified at an early stage, allowing them to be neutralized and tackled before major damage is caused, and discouraging aggressors from attacking. Intelligence plays a key role to this end. An efficient security system provides companies with integrated internal, external and public defensive capabilities to counter hybrid threats.
Discover our work and cyber Intelligence services at www.tarlogic.com