DSL Communications Interception – Introduction – Part 1
The purpose of this series of articles is to analyze communications analysis and interception strategies, specifically for DSL routers, through DSLAM devices, although it is equally valid for cable modems through CMTS.
Many of the communications over the Internet, whether at a private level, pass through communications devices provided by a DSL or cable provider and, therefore, the security of these environments is a priority aspect.
One of the last things we have been investigating at Tarlogic was the security of various routers and the underlying infrastructure that an ISP uses to provide DSL (Asymmetric Digital Subscriber Line) services. Thanks to Ebay, it is possible to acquire a large number of devices from multiple service providers around the world.
These routers have more and more computing power and functionalities but are also being more restricted to the user for reasons we will not go into here. This means that although these “smart” devices allow a large number of functions to be performed, the user has less and less control over what they do internally, who they communicate with and who attacks them.
When planning how to deal with these devices to analyze their security, without going into firmware analysis, which is also very interesting, there are usually two approaches:
- LAN analysis: Identification of services exposed to the user network.
- WAN Analysis: Identification of services exposed to Internet.
In these environments it is possible to analyze in great detail which services and protocols expose our device to different networks. This way you can probably identify vulnerabilities in web services,… but it is far from being a complete approach.
Have you ever wondered what are some ports that nmap reports open on the router and with which you are not able to interact? And how is the router updated remotely over the Internet with the latest firmware from your ISP operator?
A modern cable modem or ADSL router includes remote administration services, which allow the ISP to effectively manage the device. These services and communication mechanisms are not detectable with a traditional analysis approach. The router can also establish connection with internal ISP services, exchanging information on a regular basis, in a manner that is completely hidden from the user.
In the worst case scenario, if someone has taken control of our router, for example through a firmware modification, through a vulnerability, there is no way to identify anomalous behavior with this approach and we could be unknowingly affected by targeted malware that intercepts and steals our credentials, or allows external access to our network.
The reason why it is not possible to intercept these communications is because the traffic generated internally by the device is sent to the Internet through the telephone cable and at this point we cannot monitor the communications “directly”.
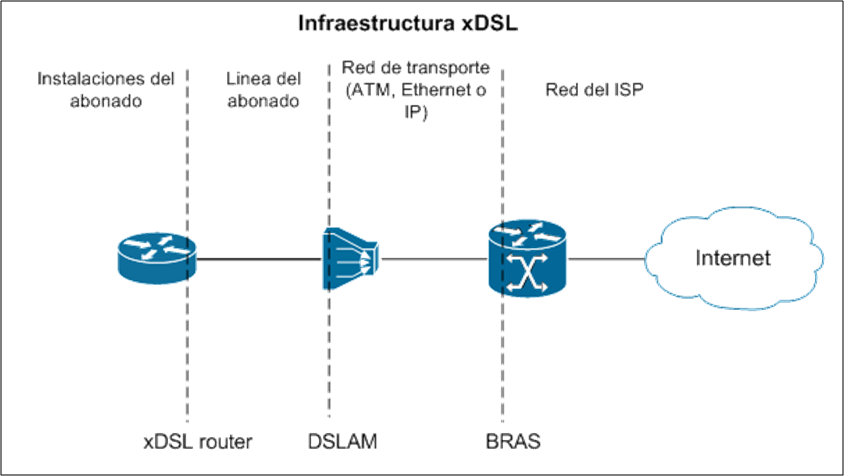
Image – xDSL infrastructure
As an initial step in setting up the laboratory, we needed to acquire a DSLAM (Digital Subscriber Line Access Multiplexer). This device, a key component in any DSL infrastructure, is nothing more than a modem that transforms the nature of the signal so that it can be transmitted from the subscriber’s routers to the operator’s facilities.
As you can see in the following image, there are different types of DSLAM (ATM, Ethernet or IP) depending on the technology used in the uplink interface, which connects the user to the provider’s facilities. In our case we chose an IP DSLAM with a maximum capacity for 8 clients.


Image – DSLAM IP
At one end of this device we have rj21 interfaces with rj11 terminators, phone cable, and at the other end an RJ45 interface.
Through this device, we can pretend to be the communications operator and intercept, effectively, any incoming and outgoing connection generated by our router.
Discover our work and cybersecurity services at www.tarlogic.com
This article is part of a series of articles about DSL Communications eavesdropping
- DSL Communications Interception – Introduction – Part 1
- Interception of DSL Communications – Synchronization – Part 2
- DSL Communications Interception – Administration – part 3
- DSL Communications Interception – TR069 – Part 4
