
TARLOGIC's BLOG
Cybersecurity - Page 2
Cybersecurity articles with security analysis and ethical hacking technics information

Hacking Bluetooth the Easy way with ESP32 HCI Commands and hidden features
This article documents the Bluetooth research line driven by Tarlogic Security as well as data on the ESP32 chip[...]
Read more
CVE-2025-1094: High vulnerability affects PostgreSQL
In recent days, a critical vulnerability (CVE-2025-1094) has been discovered in PostgreSQL that could compromise the integrity of databases in enterprise and production environment[...]
Read more
Pentesting Liferay Applications
This Pentesting Liferay Applications guide includes techniques that can be used to identify vulnerabilities and flaws in Liferay environments Liferay is a platform developed in the[...]
Read more
CVE-2024-49138: Risk in CLFS Log Handling on Windows
A high-severity vulnerability has been discovered affecting the Common Log File System (CLFS) functionality in Windows systems. This vulnerability, identified as CVE-2024-49138, al[...]
Read more
CVE-2024-53677: Critical vulnerability affecting Apache Struts
Information has been disclosed about a new critical vulnerability affecting the popular Apache Struts framework. The CVE-2024-53677 vulnerability could allow a remote attacker to e[...]
Read more
CVE-2024-52316: Critical vulnerability in Apache Tomcat
Critical vulnerability CVE-2024-52316 affecting Apache Tomcat allows authentication bypass when using the Jakarta authentication API A critical vulnerability has been identified in[...]
Read more
CVE-2024-6387: RegreSSHion, a high vulnerability that affects OpenSSH
Information has been disclosed about a new high vulnerability (CVE-2024-6387) that affects OpenSSH over Linux Servers. RegreSSHion allows an unauthenticated attacker to obtain remo[...]
Read more
Bluetooth Architecture from Scratch
The Bluetooth architecture determines which functions should be operational in an implementation and how they should be organised Bluetooth is composed of multiple technologies, pr[...]
Read more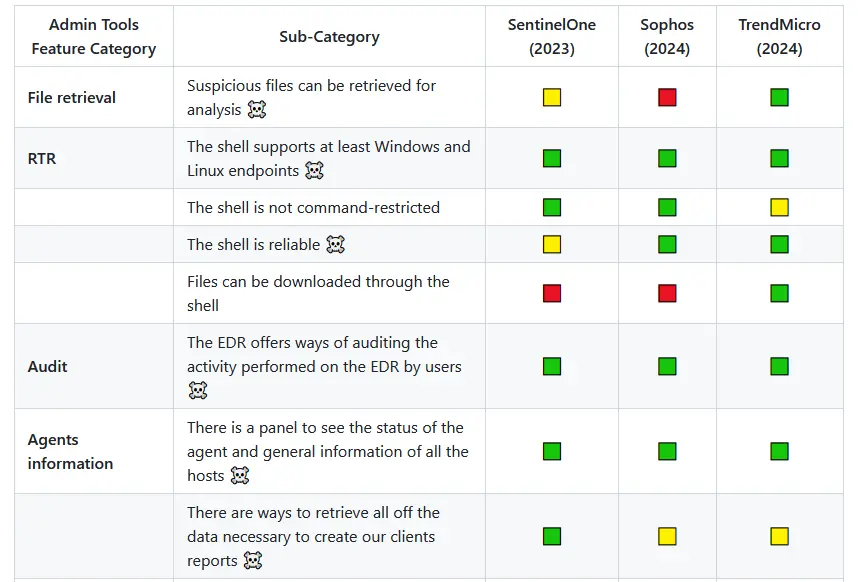
The Way of the Hunter: Defining an ad hoc EDR evaluation methodology
Nowadays Threat Hunting is a very popular term in the infosec community. However, there is not a widely shared definition of that role. Discrepancies persist as everyone considers [...]
Read more
Continuous Threat Hunting vs. Campaign-based Threat Hunting
Continuous Threat Hunting allows early detection of threats and is more complete than Campaign-based Threat Hunting The classic Threat Detection model has traditionally been consid[...]
Read more