Improving APT resilience
Table of Contents
APT Resilience Enhancement combines offensive and defensive capabilities to optimize an organization’s defensive layers
APT, or advanced persistent threat, has become increasingly common to refer to the new advanced and targeted threats facing organizations.
Behind these threats can be found a variety of actors, from foreign governments to activist groups to competitor companies looking to steal R&D and corporate information or eventually damage ICT infrastructure, for example, by deploying ransomware.
The risk of an APT in enterprises lies in the identification difficulty, which can allow it to persist for a long period on corporate systems, enabling APT operators to perform malicious actions against an organization’s interests.
A general approach to accelerating APT defensive capabilities
How resilient is an organization to a targeted APT, and are the defensive layers sufficiently optimized to respond to such a sophisticated attack?
APT Resilience Enhancement brings together offensive capabilities, such as those that could be performed by Red Team services, with the defensive capabilities that a Threat Hunting team could suggest, helping not only to answer the above questions but also to accelerate and optimize defensive capabilities in terms of detection, containment and response.
The process of accelerating detection and response layers against an APT involves the execution of the following sequence of activities for the best integration of the offensive techniques of an APT in the defensive layers:
A particular approach to compromise using APTs
An APT compromise involves a targeted and highly specialized attack against an organization designed to maintain continuous access over time. This type of exercise is characterized by using different entry vectors, such as zero-day vulnerabilities or phishing attacks against specific employees of an organization, among others.
The final design of the APT compromise exercise must be agreed upon before the start of the exercise and requires advanced malware with sophisticated infection capabilities, control of compromised computers, concealment of malicious activity, pivoting for lateral movement, the elevation of privilege and persistence, among other qualities, and a highly specialized team capable of operating the service.
During the execution of the APT compromise exercise, the Tarlogic Security team performs, in a controlled manner, a targeted attack against an organization to gain access to its corporate infrastructure through previously agreed entry vectors and deploy an APT specially designed to:
- Infect corporate systems.
- Perform lateral movements on the organization’s systems.
- Elevate privileges where required.
- Maintain persistence that allows the control of compromised computers over time.
- Carrying out previously agreed impact activities, such as:
- Identifying and exfiltrating sensitive information.
- Deployment of Ransomware
- Any other pre-agreed impact actions
Particular focus on identifying and designing APT resilience improvement opportunities
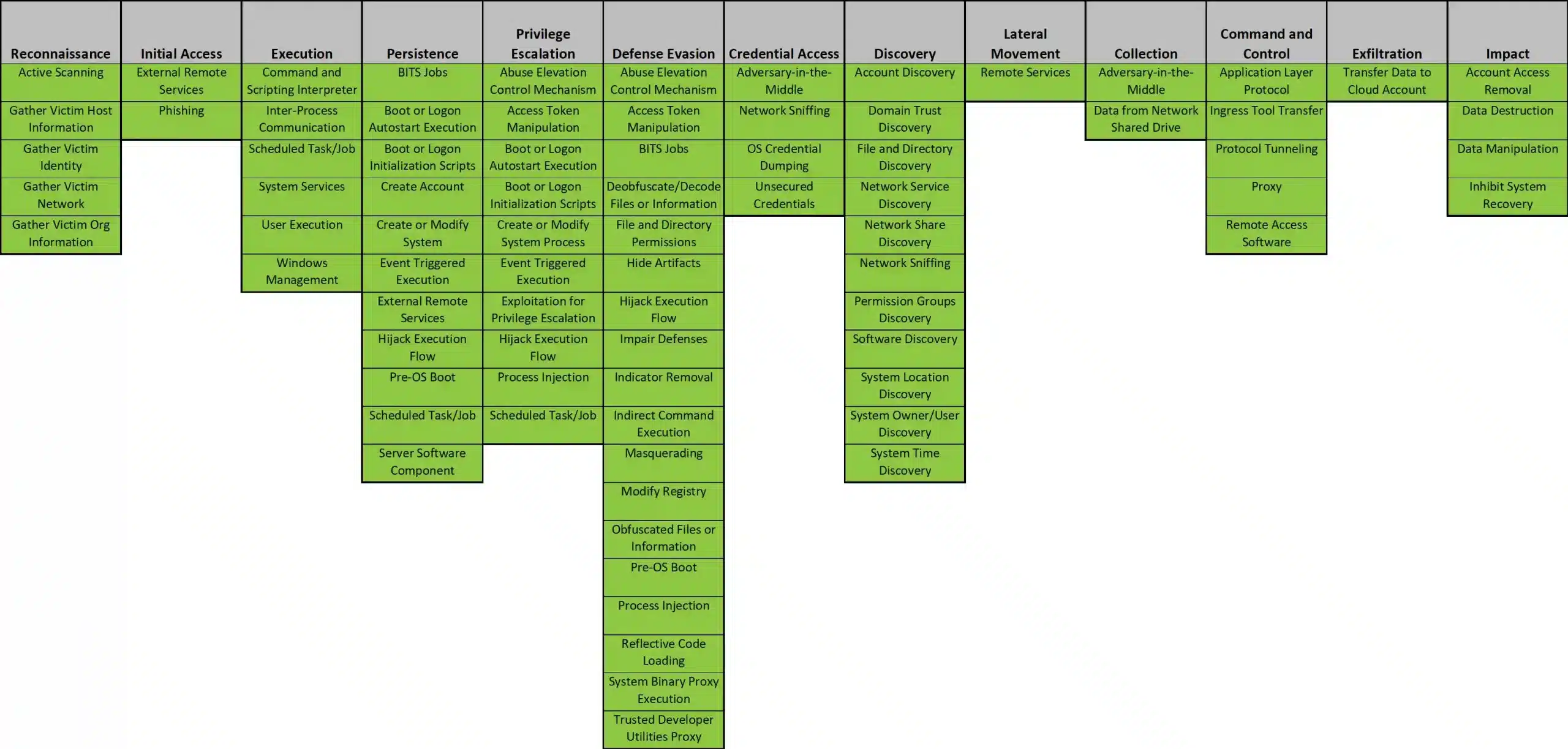
Our Threat Hunting team constantly monitors the main APTs and studies the TTPs they may use, building an important Threat Hunting Intelligene™ knowledge base that can be easily exported to any organization.
Since the daily work of the Threat Hunting team is focused on researching malicious techniques and identifying and designing detection opportunities, this positions us as an essential accelerator to apply all our defensive knowledge against APT attacks.
In this way, as new TTPs used by APTs are tested, and detection improvements are designed, we are helping organizations to build strong defense capabilities. In addition, this approach has enabled us to provide Proactive Threat Hunting strategies for the detection of the main APTs in use today, as summarized below:
For each TTP employed by the APT, we should ask ourselves the following questions to determine the level of resilience of an organization:
- Is there telemetry associated with the TTP?
- Has an alert been generated, or is there an effective process to detect the TTP and confirm its malicious nature?
- Has the case been investigated to both the root cause of the compromise and the full impact received?
Many organizations can only answer yes to the first question, meaning they have the technology to deal with an APT successfully but need to use it effectively. Overcoming this state of resilience is one of the main challenges we see today; hence, implementing APT Resilience Improvement is of great value.
Benefits of a TPA engagement exercise
In line with the above, our APT engagement exercise approach maximizes that the defensive layers absorb the full value of the exercise. This makes it possible to get the most out of the investment dedicated to this type of exercise because:
- It allows for assessing the risk in a sophisticated targeted attack.
- It helps to know the capabilities of detection and response to APT and, therefore, to objectify the level of resilience of an organization concerning targeted attacks.
- Estimates the maturity level of the organization’s defensive capabilities and the coordination of the different teams and their incident response processes by detecting, containing and mitigating the risk of this type of threat.
- Identifies possibilities for improving defensive layers at the technical and procedural control levels.
- Accelerates the training of Blue Team, Threat Hunting or SOC teams that the organization may have.