Memory Reader: obtaining access keys from IoT devices
Table of Contents
IoT devices are becoming more and more widespread and established in domestic environments. They help us in our daily lives and allow us to perform numerous functions that until a few years ago were unthinkable, such as controlling the heating remotely, the lights from the cell phone or interacting with a smart speaker or TV to play the music or series we want to listen to or watch.
Depending on the different functionalities of the IoT devices, their design can be more or less complex. However, they all share a common element, they make use of small memories to store the firmware that governs their operation. Unfortunately, the anatomy of these memories is not generic. While it is true that most devices implement standardized memories, there are some manufacturers that make use of memories with particular form factors and whose reading is not a trivial task as it is not possible to get an adapter for it.
This blog post will introduce an indispensable and very common tool in the context of hardware hacking: memory readers. In addition, we will also present some conclusions on the importance of properly securing the data contained in memory and the dangers associated with bad practices during the process of bastioning IoT devices.
The dominant trend in the IoT sector today is to implement flash memory in devices, mainly because of its low cost and simplicity of use. Three memory families can be distinguished depending on the type of communication interface they implement: I2C or SPI in addition to the eMMC standard.
| Memory interface | Capacity | Price |
| I2C | Maximum of 1Mbit | Lowest price |
| SPI | 1 Mbit to 4 Gbit | Best price/capacity ratio of all three |
| eMMC | 256 Mbits – 16 Gbits (can have more capacity, although it is not usual) | Highest price |
Currently, the trend in IoT devices is increasingly oriented towards eMMC type memories as developments are becoming more complex and need to store more complex software that does not fit in low-capacity storage memories.
While it is true that the only way to check the type of memory that a device is equipped with is to open it and check it visually, here are some approximations that can help us to intuit in advance the type of memory that is expected to be found:
- Cheaper devices usually require less memory and are usually equipped with cheaper I2C or SPI type memories.
- When devices require less than 1 Gigabit of data, they are almost always equipped with SPI type memory.
- If the memory capacity required by the device exceeds 1 Gigabit, depending on the manufacturer’s cost estimate, the number of batches to be manufactured and the number of units per batch, SPI or eMMC type memories may be used. However, the current trend among manufacturers is towards eMMC memories because their form factor is more standardized and they allow hardware upgrades (memory expansion of the device) without interfering with or impacting the rest of the device’s components.
After explaining the types of memories that exist, one might ask, what are the risks of accessing the contents of these memories, and how can we access them?
Risks arising from access to memory information
Determining the risks associated with unauthorized access to the information contained in memory is not a trivial task and depends on many factors that will be listed below.
On the one hand, from the device manufacturers’ point of view, it is dangerous for a third party to gain access to the contents of the memory because, if the memory is not properly secured, an attacker could gain access to the binaries running on the device. Once the versions of the binaries implemented by the device are known, the search for potential vulnerabilities associated with the device is greatly narrowed down.
In addition, having direct access to the firmware binaries opens up another avenue of attack for a potential attacker, namely reverse engineering. In case no public vulnerability is found affecting the versions of the binaries running on the IoT device, being able to reverse engineer them facilitates the discovery of 0-day vulnerabilities. It is important to emphasize that it facilitates their discovery, but does not necessarily guarantee it.
Another important point to keep in mind is that if it is easy to read these memories, it will also be easy to write, so that if it is not secured, it is possible to modify or alter all or part of the software running the device so that we can have full control of what it does with a simple modification.
Regarding current trends in the IoT sector, from the Tarlogic Innovation team we have found manufacturers that encrypt the firmware (the contents of the memory) and unpack and decrypt it at runtime during the loading process; and many others that do not add this security layer. Other manufacturers, on the other hand, make use of hybrid solutions and encrypt only some sectors and/or partitions of the memory.
On the other hand, as far as the user is concerned, beyond the risk of vulnerabilities being discovered that may affect the devices he has purchased, there are other potential risks that need to be taken into account, which will be discussed below.
Extract sensitive information from IoT devices
The first of these is related to the privacy of user data. If the device does not encrypt the contents of the memory and the user loses it, it is possible to extract sensitive information from it, such as: access credentials to certain services, users and passwords, keys to the Wi-Fi networks to which it is connected, etc.
The impact of having access to this type of data may seem low or almost negligible since it implies the theft of the device and in domestic environments this type of case is not usually common. However, when the IoT device is in an enterprise environment everything changes. Having access to this type of data can represent a significant and dangerous security breach for the company.
The second risk is that other functionalities can be maliciously included in the device. Some time ago there was a widely publicized news item about a network of people using demo computers displayed in different stores and commercial chains in Spain to mine cryptocurrencies.
While it is true that IoT devices are generally low performance and cannot be used for this type of purpose, if the memories are not encrypted and no integrity control is implemented, there is no impediment for an attacker to extract the memory, modify it to incorporate some illicit service/functionality, and then reload it. The user would not be aware of this new functionality and the attacker could take advantage of it.
Finally, the third risk of IoT devices is related to lateral movements. As they are connected to the Internet, if one of these devices is vulnerable to an attack, it is possible that the attacker can pivot within the network and attack other devices in the network at a later time. As countermeasures to prevent this type of behavior, today there are routers that have an isolated network for IoT devices (although this is not always the case).
To conclude this section, the following are some common situations that the Tarlogic Innovation team has encountered during the IoT security audits and that pose a high security risk:
- Failure to check memory integrity.
- Failure to use the cryptographic capabilities built into almost all microprocessors/microcontrollers today.
- Do not encrypt sensitive memory partitions.
- Use simple and easy-to-break ciphers (e.g. base64).
- Do not delete sensitive information such as encryption keys (public and private) from the firmware.
- Use an encryption key that is stored somewhere in the system (hardcoded passwords).
- Writing network configurations and/or cloud access keys in clear text files.
- Existence of access gateways for device maintenance (backdoors) with a low level of security.
- Exposing services on non-conventional ports with proprietary and non-secure protocols.
Firmware extraction: memory readers
After assessing the risks associated with accessing the firmware (memory contents), it is legitimate to ask what procedure should be followed to be able to read the memory. There are various commercial solutions for reading memory. The main problem with this type of reader is that they are closely linked to the type of memory to be read, and in many cases adapters for specific rare memory formats are not commercially available. In fact, it is quite common to have to buy different models of memory readers just because the one you have is not compatible with a particular memory format.
Tarlogic’s Innovation team has developed a memory adapter that allows reading memory that makes use of the three interfaces mentioned at the beginning of the article (I2C, SPI and eMMC). It currently supports I2C and SPI protocols, and a hardware and software interface for eMMC will soon be available.
Thanks to this tool, it avoids having to depend on commercial memory readers, providing greater flexibility, especially when working with memories that are outside the most widely used standards.
Tool description
The form factor of the developed tool allows it to be connected to a Raspberry Pi (models 3 and 4). Although it is intended to be used as a complement to the Raspberry, it is possible to use it with other development boards and mainstream solutions such as an Arduino. For this purpose, the tool has been designed with male / female headers type connectors to ensure compatibility with as many acquisition systems as possible, increasing the flexibility of the tool.
The hardware developed has support for SPI and I2C Flash memories and has read support in the 25 range (SPI), the 24 range (I2C) is being improved and support for the eMMC standard is in the testing phase.
To ensure the modularity of the proposed hardware solution, an intermediate board has been designed to adapt the memory reader to the Raspberry and power both. This board has power connectors and adaptation for reading memories.
In the following images you can see the top and side view of the intermediate board (or motherboard).
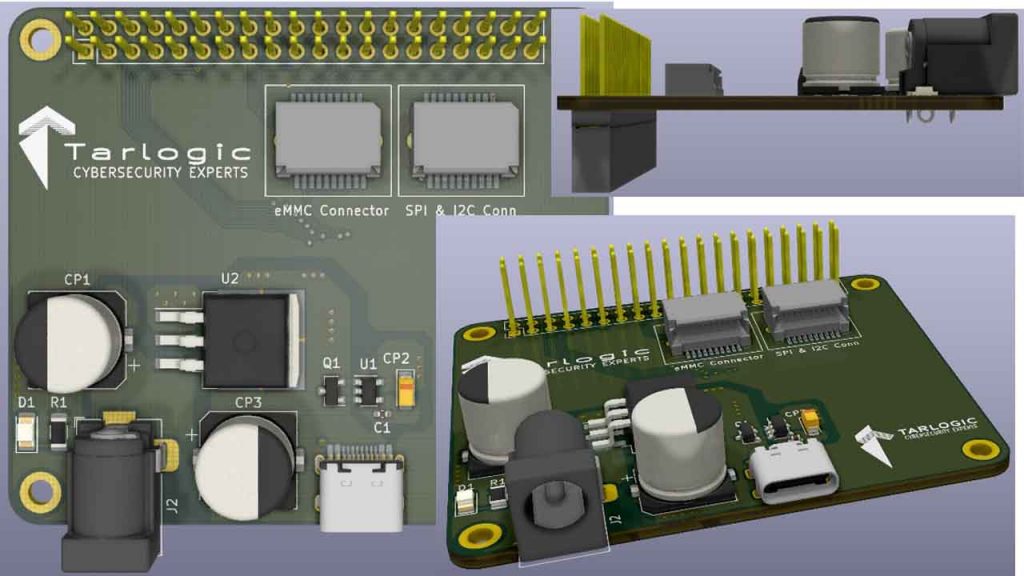
With modularity in mind, header connectors have been equipped for connection to the Raspberry. It has two power connectors that allow powering from a 12V and 2.5 mm power supply or mobile charger with USB C plug (both the Raspberry and the memory reader).
The main elements that make up the board are:
- 2×20 male / female headers type connector with standard Raspberry Pi pin configuration.
- 12V power connector type Barrel Jack 2.5mm to power the Raspberry Pi and the memory reader.
- USB C power connector for the same purpose, powering both devices.
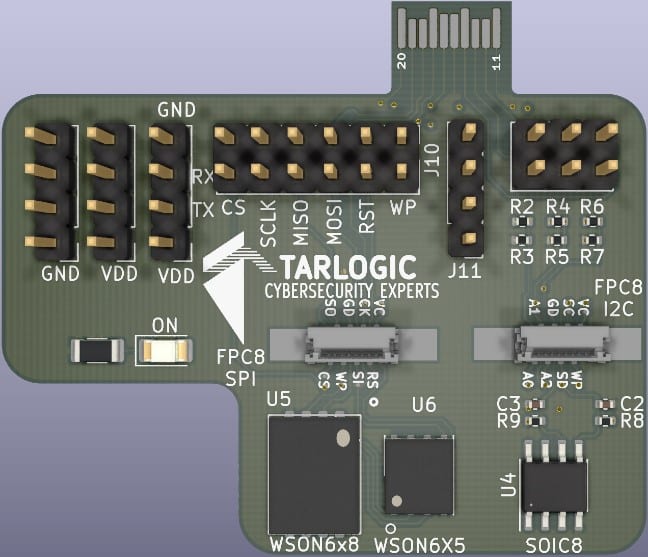
- Board edge connectors (such as RAMs or PCI cards) – intended to support daughter cards. SPI and I2C interfaces are arranged on the right connector and for eMMC type memories the connector on the left.
A daughter board is connected to the mother board via board edge connectors. The memory to be read is placed on this daughter board. In the case of needing to read memories with different form factors, it is only necessary to design a daughter board to read these memories, and the primary board can be reused.
You can see the design of the current adapter for SPI and I2C memories and a model for memories in uncommon format in the images below.
- Card edge connector to connect to the motherboard.
- Power and debug inputs/outputs from the Raspberry.
- An FPC8 SPI connector is the vertical 8-pin FPC (flexible printed circuit) type with 0.5 mm pitch to be able to make use of adapter clips on SPI flash memories since some IoT devices have this type of connectors to plug in.
- Footprint for WSON6x8 memory with SPI interface.
- FPC8 I2C vertical 8-pin FPC type connector with 0.5 mm pitch to make use of adapter clips on I2C flash memories.
- Footprint for SOIC 8 memory with I2C interface.
What are the benefits of in-house designs over commercial solutions?
The main benefit of using proprietary solutions is the flexibility they provide compared to commercial solutions that are limited to the memory adapters supported by companies dedicated to the manufacture and sale of readers and that mainly cover only the most used and commercially interesting ones.
Thanks to the hardware/software tools developed by Tarlogic, any type of memory can be read, only the new daughterboard has to be designed with the necessary footprint, speeding up the research and auditing work. Moreover, by seamlessly integrating with today’s common and accessible devices such as the Raspberry Pi, its potential increases exponentially.
Discover our work and cybersecurity services at www.tarlogic.com