How to integrate security into the web application development cycle

Prioritizing security in the web application development cycle is essential for detecting and resolving vulnerabilities and preventing serious security incidents
A critical vulnerability in WP Ghost, a security plugin for the WordPress web content management platform that has been installed on more than 200,000 websites worldwide, would allow remote code execution by malicious actors.
This alarming news highlights the role that security plays in the web application development cycle.
From the moment you start planning a website until it is no longer in operation, it is essential to prioritize its protection against possible attacks and carry out web security audits to discover vulnerabilities in any of its components.
Below, we will break down how security can be integrated into the web application development cycle.
1. What is the web application development cycle?
Human beings tend to think linearly. However, our lives are full of cycles. This reality is clearly evident in the field of web application development. Why?
Creating a website is not a straight-line process that begins with planning and ends when it is launched or goes live. This is because web development is an area that is constantly evolving. Throughout the life of a website, it must undergo periodic improvements to optimize its performance and, above all, ensure an optimal level of protection.
That is why security in the web application development cycle is so important.
What phases make up this cycle?
As a general rule, it is considered to encompass the following processes:
- Planning. In this phase, the requirements of the web application are established, and a programming plan is drawn up for its development.
- Design. The technology and development tools to be used are established, as well as the necessary architecture.
- Coding. In this phase, the website code is developed, for which it is common to use existing components from third-party libraries.
- Testing. Companies that develop web applications must carry out tests to check that they work optimally and that there are no vulnerabilities in the code. There is usually no testing phase as such, but rather testing is carried out while the web applications are being developed.
- Production deployment. Once the website has passed all tests, it must be moved from the test environment to the production environment.
- Maintenance. Websites require ongoing maintenance to ensure they function optimally, fix bugs, incorporate improvements, and resolve security issues. This involves restarting the cycle to design, develop, and test improvements before deploying them to production.
2. Zero-day vulnerabilities and software supply chain attacks: SDLC security is a strategic necessity
Security in the software development cycle in general, and web applications in particular, has become a priority for developers and companies that purchase third-party applications. Why?
- Web applications are critical assets for millions of businesses.
- Cyberattacks against all types of companies have continued to grow in recent years.
- Websites are business assets with a high level of exposure.
- The consequences of successful attacks against web applications can include paralysis of business activity or the exfiltration of private data.
Added to this are two key cybersecurity trends today: the rise of attacks that exploit zero-day vulnerabilities and software supply chain attacks.
The only way to effectively combat these attacks is to integrate security into the web application development cycle. This allows you to:
- Find weaknesses in code and components on a website before they go live.
- Detect vulnerabilities affecting a web application before they are discovered and exploited by malicious actors.
- Develop and implement security patches as quickly as possible to address newly discovered vulnerabilities.
- Continuously optimize the security posture of web applications.
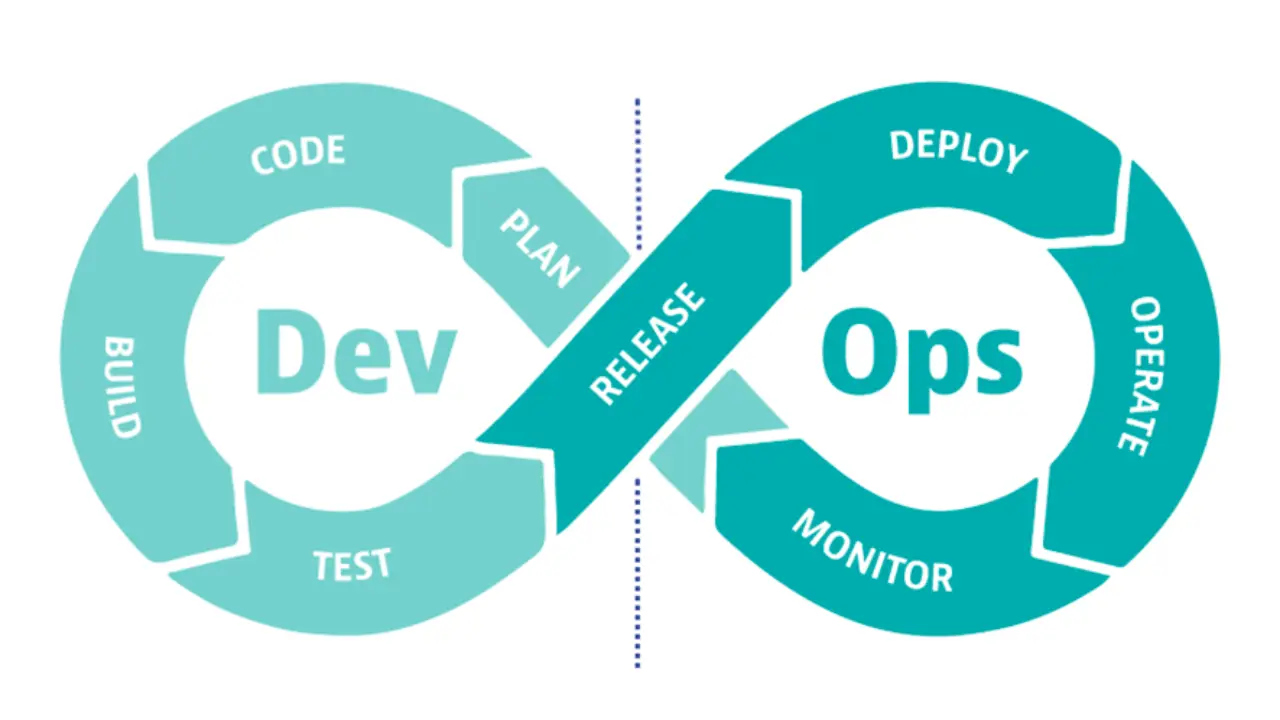
3. DevSecOps: Prioritize security in the web application development cycle
To integrate security into the web application development cycle, companies can implement a DevSecOps (Development, Security, and Operations) strategy.
The DevSecOps approach advocates security testing at all stages of the web lifecycle and the use of best practices in development.
To facilitate the implementation of a DevSecOps strategy, the OWASP Foundation, a global methodological benchmark, is developing a guide to help developers and enable companies to “detect security issues (whether design flaws or application vulnerabilities) as early as possible.”
One of the concepts within DevSecOps that is gaining prominence is Shift Left, which seeks to focus attention and resources on security in the early stages of the vulnerability lifecycle, enabling faster and more efficient action when vulnerabilities are found.
Where should a DevSecOps strategy focus?
- People. Developers must be trained in security and follow secure coding practices.
- The development process itself:
- The need to carry out threat modeling during the design of a web application.
- Perform security tests such as static source code analysis (SAST) or software composition analysis (SCA) during the code creation process.
- Before an application goes into production, dynamic application security testing (DAST) must be performed.
- During the maintenance of a web application, it is essential to carry out effective vulnerability management and use cybersecurity services such as penetration testing to test its security mechanisms.
- Governance. It is vitally important to check compliance with current regulations, especially in the area of data protection.
4. What services allow us to integrate security into the web application development cycle?
How can developers and companies that purchase web applications strengthen their security throughout their lifecycle? By using cybersecurity services that allow them to detect, manage, and resolve vulnerabilities to prevent them from being successfully exploited.
- Source code audit. This is used to track security flaws in the code of a web application using static analysis techniques.
- Web security audit. This type of analysis can identify weaknesses in web applications so that they can be corrected. A web security audit can detect vulnerabilities related to business logic, or information flows that go unnoticed by automated tools.
- Vulnerability management and detection of emerging vulnerabilities. Integrating security into the web application development cycle involves continuous vulnerability management, taking into account the likelihood of exploitation and impact. In addition, continuous monitoring of discovered vulnerabilities allows for effective management of zero-day vulnerabilities.
- Penetration testing services. Given the importance of web applications for businesses, it is advisable to subject them to advanced intrusion tests to detect security flaws, measure the impact of their exploitation, and obtain a list of recommendations to optimize their level of protection.
Conclusions: 5 compelling reasons to integrate security into the web application development cycle
- Detect vulnerabilities in the early stages of the development cycle.
- Reduce the costs of fixing security flaws when they are found after websites are already up and running.
- Maintain an optimal security posture throughout the life of an application.
- Prevent security incidents and limit their impact.
- Avoid the financial, reputational, and legal consequences of a serious incident.
