
Red Team Tales 0x02: from SQLi to Domain Admin
One of the activities included in the operation of the Tarlogic Red Team is the search for vulnerabilities in the softwa[...]

Red team & Threat hunting Blog - offensive security


One of the activities included in the operation of the Tarlogic Red Team is the search for vulnerabilities in the softwa[...]

Introduction In a Red Team operation, a perimeter asset vulnerable to SQL Injection was identified. Through this vulnera[...]
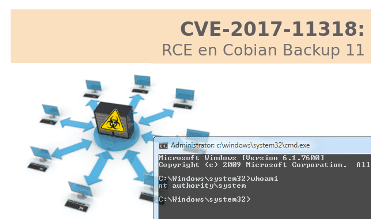
During a Tarlogic Red Team operation, a serious vulnerability was discovered in Cobian Backup software (CVE-2017-11318) [...]
Web servers exposed to the Internet are a traditional entry point during penetration tests and Red Team operations. Ensu[...]

The creation of a keylogger in PowerShell during the development of a Tarlogic Red Team operation was necessary. And giv[...]
In the last edition of HackRon, in our talk “The Red Team always wins” we tackled some techniques used duri[...]