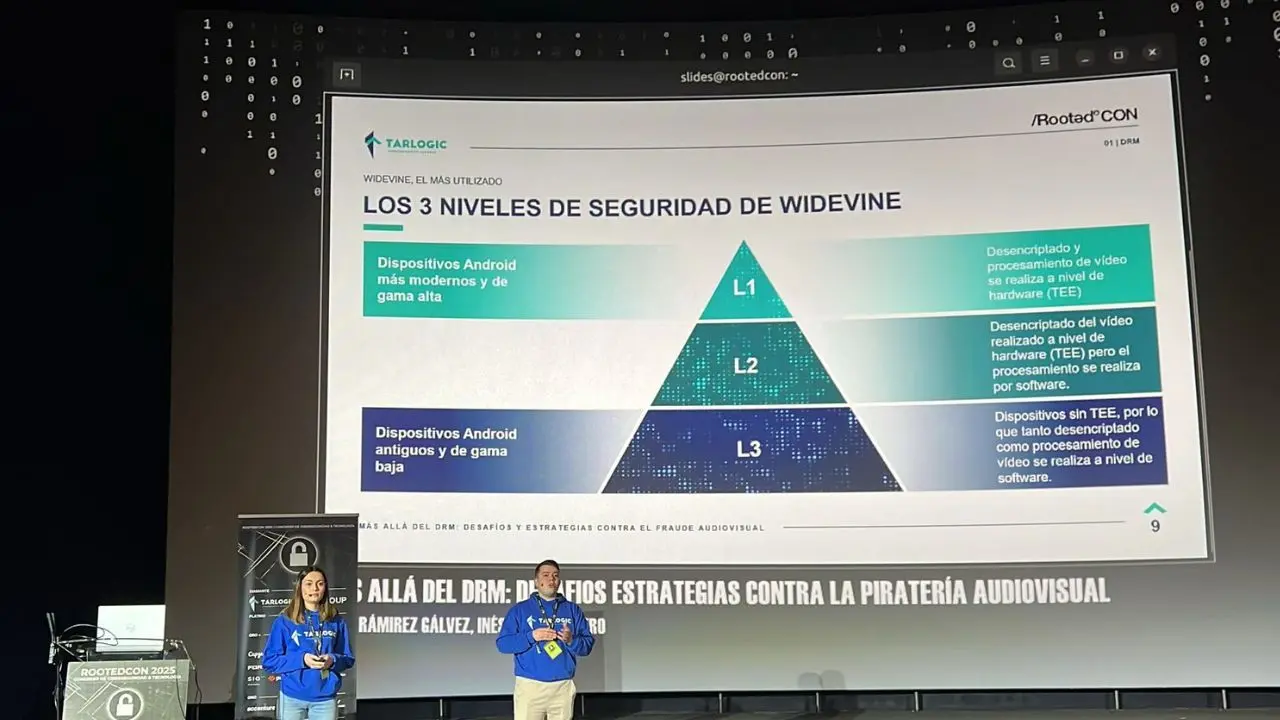
CVE-2024-58101
CVSS v4.0 Score: 8.5 / High Samsung Audio devices are Bluetooth pairable by default without user input nor a way to stop this mode. Vendor: SamsungProducts: Galaxy Buds, Galaxy Buds 2Discovered by: Antonio Vázquez Blanco (@antonvblanco), Jesús María Gómez MorenoPublic fix: NoProof of Concept: https://github.com/TarlogicSecurity/BlueSpy Summary: Samsung Galaxy Buds and Galaxy Buds 2 are earphones that are pairable by default without requiring user interaction or a way to avoid it. Details: Devices fail to pass the following BSAM controls: BSAM-PA-01 - Pairable mode by default BSAM-PA-02 - Input and output capabilities BSAM-PA-04 - Rejection of legacy pairing BSAM-PA-05 - Pairing without user interaction Impact: This allows for device pairing without user consent nor user notification, leading to take full control of device. As a consequence, audio ...