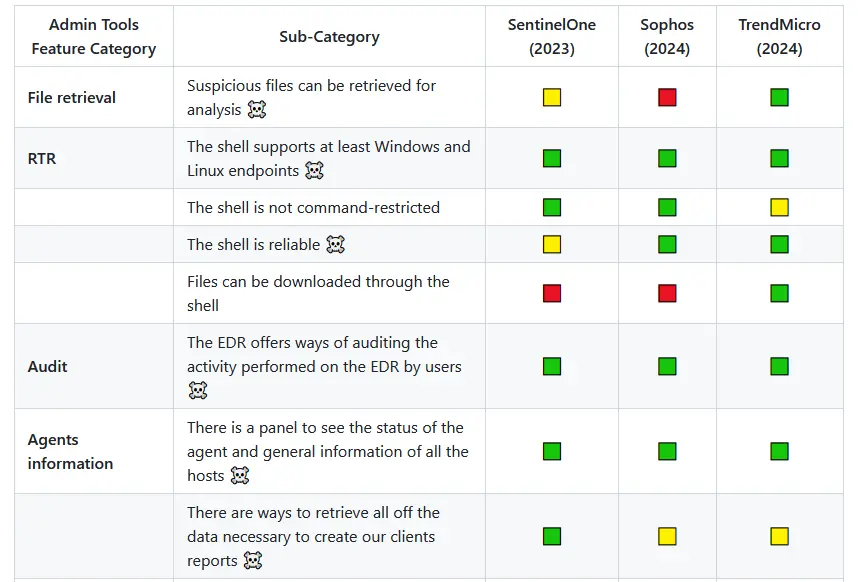
The Way of the Hunter: Defining an ad hoc EDR evaluation methodology
Nowadays Threat Hunting is a very popular term in the infosec community. However, there is not a widely shared definition of that role. Discrepancies persist as everyone considers their own implementation as the right way to do it. Nevertheless, although the sector has yet to agree officially on what exactly entails to be a Threat Hunter, and which is their scope of action, there are some aspects in which consensus has been reached. First, Threat Hunting has an implicit proactive nature that does not share with the traditional cybersecurity defence roles. Companies used to be restricted to take all the preventive and reactive actions available to protect their infrastructure and hope for the best: avoiding being compromised or at least ...