What are “Watering Hole Attacks”?

The term “watering hole attack” refers to a strategy used while running targeted attacks campaigns where APT distribution is done using a trusted website which is usually visited by company employees or a target entity. Please, consider the following example:
A hydro-electric company is headquartered in a particular european region. In this region several regional newspapers are published daily. Usually, employees of that office block visit the online edition of those newspapers every day. Actually, this behavior was detected by a group of people aiming at stealing business strategic information while gathering information process.
So attackers analyze those newspapers looking for vulnerabilities and detect the possibility of injecting a malicious code in those web ads shown to every visitor in one of the newspapers. Consequently, they take advantage of this vulnerability to introduce a script detecting visitor’s origin and if the proxy IP used is the same as the hydro-electric company’s one, they run an exploit in their browser.
In many occasions, security measures adopted by companies – at engineering and employees training level – make difficult to carry out an intrusion using conventional models such as vulnerabilities exploitation in external elements or spear phishing campaigns. In these cases, it could be easier and more effective to compromise a third-party web which is often visited by employees and therefore, use it a as a means of APT distribution.
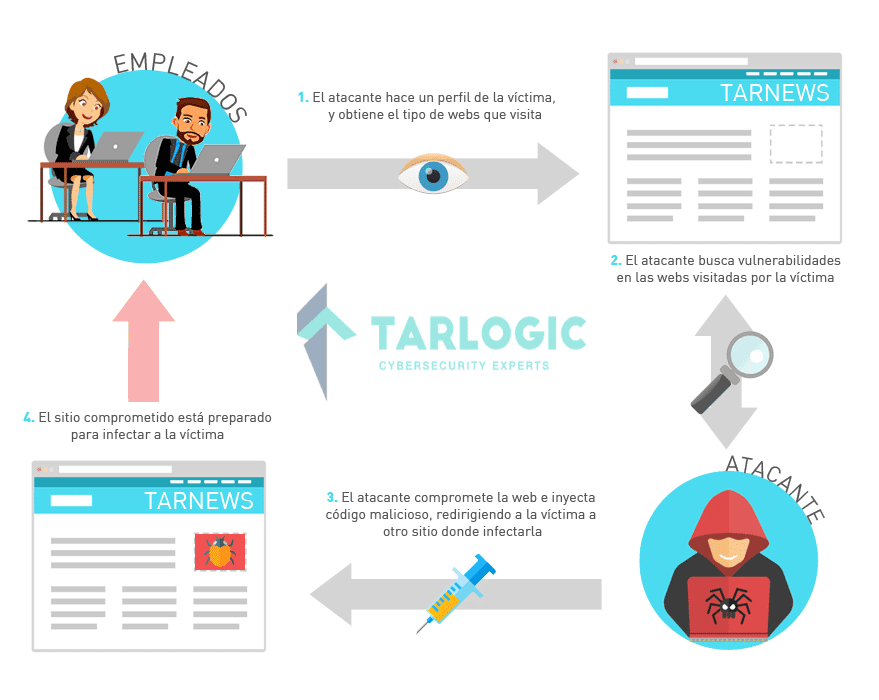
In these scenarios the agents expecting to introduce APT in the target company, carry out a deep study about workers’ routines, pinpointing key websites due to frequency of use and trust. Once the potential target webs are analyzed, it is time to start looking for vulnerabilities which exploitation enables the introduction of malicious code which shall be run by visitors.
Attackers could exploit vulnerabilities on the client’s side using the introduced code in the web. Therefore, malware installation is invisibly forced. Also, they can take advantage of the existing trust relation between an employee and a web to run the APT download using social engineering.
Watering Hole Attack impact
This compromising approach of a trustee third-party acting as an intermediary has many advantages over a direct attack against companies. Usually, users lower their defenses in those websites which are often visited, being then more easily infected. A good employee training in confluence with automated inbox mailing analysis could prevent successfully a conventional spear phishing campaign. However, if external webs which are often visited are used, introducing malware into a corporate network it is only a matter of time.
Additionally, due to trust it is much more difficult to track the origin of an intrusion in case of detecting anomalies generating malware. Then, it is very difficult to guess the real origin of the infection once the attack is hidden in regular traffic.
Discover our work and cybersecurity services at www.tarlogic.com
