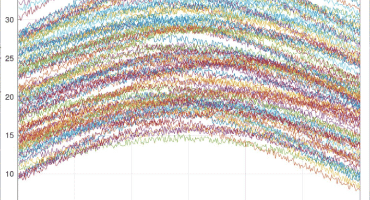
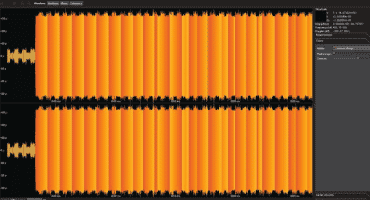
Security in PRIME networks – Current status
Since January 2019, all electricity meters for low power customers (up to 15 kW) in Spain are (or have been replaced by) smart electricity meters, allowing distributors to carry out consumption measurements and various supply point management operations remotely. Half of the smart electricity meters in the Spanish market use a PLC communications stack based on PRIME 1.3.6 in the lower layers and DLMS in the application layer. In March 2020, Tarlogic presented the results of its research about the security of these networks at the RootedCON of the same year, demonstrating that traffic at the PRIME level was not encrypted and that, at the DLMS level, although some traffic was exchanged encrypted (using dedicated keys), most of it remained ...